Ever heard the term ‘RDP’ or ‘Remote Desktop Protocol’ and wondered exactly what it means? Maybe your IT department uses it, you need to work from home, or you’re just exploring tech terms. You’ve come to the right place! This friendly guide will break down what RDP is.
We’ll explore how it works its magic to let you control another computer remotely. We will also cover why it’s such a widely used tool in the tech world. Everything will be explained in simple, easy-to-understand language. Let’s dive in and demystify Remote Desktop Protocol together!
What Exactly is Remote Desktop Protocol (RDP)?
Remote Desktop Protocol (RDP) is a secure network communications protocol developed by Microsoft. It allows a user to connect to and control another computer over a network connection. Think of it like having a long, invisible cable connecting you to another PC.
Essentially, RDP lets you see the remote computer’s screen (desktop) on your own device. You can then interact with it using your mouse and keyboard, almost as if you were sitting right in front of it. This capability is fundamental for remote access scenarios.
The acronym RDP stands simply for Remote Desktop Protocol. A protocol is a set of rules or standards that govern how devices communicate. RDP specifically defines the rules for transmitting display information, keyboard inputs, mouse movements, and other data between two computers.
Microsoft initially introduced RDP with Windows NT 4.0 Terminal Server Edition. It has since become a core technology integrated into most professional versions of the Windows operating system. Its widespread availability in Windows contributes significantly to its popularity for remote connections.
Imagine you need a file from your powerful desktop computer at the office, but you’re at home with your laptop. RDP provides a way to log into your office PC remotely. You can then access files, run applications, and perform tasks just like you would locally.
This protocol is the foundation for features like “Remote Desktop Connection” found in Windows. While often used interchangeably by users, RDP is the underlying technology, and Remote Desktop Connection is the client software used to initiate an RDP session. Understanding this distinction clarifies how remote access is achieved.
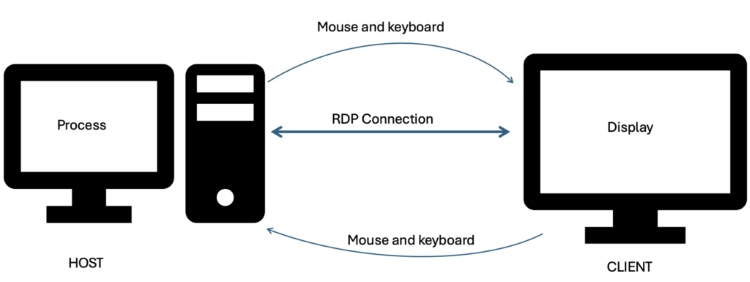
How Does RDP Work? A Simple Look Inside
Understanding how RDP functions involves looking at its core components and processes. It primarily uses a client-server model to establish and manage the remote connection. This model is common in network applications, enabling resource sharing and communication between different machines efficiently.
The Client and Server Connection
An RDP connection involves two main components: an RDP server and an RDP client. The server is the computer you want to connect to – the remote machine whose desktop you wish to access and control. This machine runs the RDP server software, listening for incoming connection requests.
The client is the device you are connecting from – your local computer, laptop, tablet, or even smartphone. This device runs the RDP client software, such as the “Remote Desktop Connection” application built into Windows. The client initiates the connection to the server.
Think of the server as the host computer offering its resources (its desktop environment). The client is the guest computer requesting access to those resources. The RDP protocol manages the entire conversation between these two components, ensuring data flows correctly and securely.
When you start an RDP session, your client software reaches out across the network to the specified server. The server verifies if it accepts connections and, if security settings allow, begins the communication process defined by the Remote Desktop Protocol rules. This establishes the remote session.
Talking Through Port 3389
By default, RDP communicates over network port 3389. A network port is like a specific numbered doorway on a computer used for certain types of network traffic. Think of an office building with many doors; each door (port) leads to a different service or application.
When an RDP client wants to connect to an RDP server, it sends its request specifically to port 3389 on the server’s network address (IP address). The server listens on this port for incoming RDP connection attempts. This standardization allows RDP traffic to be easily identified.
While 3389 is the default, administrators can change the RDP listening port on the server for security reasons. This practice, known as port obfuscation, can help hide the RDP service from automated scans looking for open default ports, adding a minor layer of security through obscurity.
Firewalls, which act as security guards for networks, must be configured to allow traffic through port 3389 (or the custom port, if changed) for RDP connections to succeed. Blocking this port effectively prevents remote desktop access via RDP to that machine or network.
What Gets Sent?
During an RDP session, various types of data are exchanged between the client and server. The most crucial data is the graphical display information from the server. RDP transmits an optimized representation of the server’s screen output back to the client device, allowing you to see the remote desktop.
Simultaneously, your actions on the client device – keyboard presses and mouse movements – are captured and sent to the server. The server processes these inputs as if they were performed directly on the remote machine, enabling you to interact with applications and the operating system.
RDP is designed to be efficient over various network speeds. It uses techniques like data compression and caching bitmaps (graphical elements) to reduce the amount of data that needs transmission. This optimization helps provide a smoother user experience, especially over slower connections like the internet.
Beyond screen data and input, RDP can also redirect other resources. This includes things like printers (allowing you to print from the remote session to a local printer), audio (playing sounds from the remote PC on your local speakers), and even local drives (making them accessible within the remote session).
This multi-channel capability makes RDP quite versatile. It handles not just the visual and input data but also peripherals and clipboard sharing (copy/paste between local and remote machines). All this data travels securely within the encrypted RDP connection channel.
Why Use RDP? Common Scenarios & Benefits
Remote Desktop Protocol offers significant advantages for various situations. Its ability to provide full graphical access to a remote machine makes it indispensable for individuals and organizations needing remote capabilities. Let’s explore some common scenarios where RDP shines.
Working From Home or Anywhere (Remote Work)
RDP is a cornerstone technology for enabling remote work. It allows employees to securely connect to their office workstations or virtual desktops hosted in a data center from their home computers or laptops. This provides access to corporate applications, files, and resources seamlessly.
Imagine needing specialized software only installed on your powerful office desktop. Instead of needing that software on your home laptop, you can use RDP to connect to your office machine. You run the software remotely, seeing the interface and interacting as if you were physically there.
This approach centralizes data and applications on company-managed systems, enhancing security compared to storing sensitive files on potentially less secure personal devices. Employees get the full functionality of their work environment, regardless of their physical location, promoting productivity and flexibility.
Many organizations deploy virtual desktop infrastructure (VDI) solutions that heavily rely on RDP or similar protocols. Employees connect via an RDP client to a personalized virtual machine (VM) running in the company’s data center, providing a consistent and managed desktop experience from anywhere.
The COVID-19 pandemic accelerated the adoption of remote work models, highlighting the critical role of technologies like RDP. A 2023 survey by Owl Labs indicated that a significant percentage of workers globally continue to work remotely or in hybrid arrangements, often relying on remote access tools.
Getting Help: IT Support & Troubleshooting
RDP is an essential tool for IT support teams. It allows technicians to remotely connect to users’ computers or company servers to diagnose problems, install software, configure settings, and perform maintenance without needing to be physically present. This saves significant time and resources.
Consider a user experiencing a software issue. Instead of trying to explain the problem over the phone, they can grant an IT support technician RDP access. The technician can then see the user’s screen, control the mouse and keyboard, and troubleshoot the issue directly.
This “see-what-I-see” capability drastically improves troubleshooting efficiency and accuracy. Technicians can observe error messages, check system logs, and replicate issues firsthand. This leads to faster problem resolution and reduced user downtime, enhancing overall productivity and user satisfaction.
For managing servers located in data centers or remote offices, RDP is invaluable for administrators. They can perform routine maintenance, apply updates, monitor performance, and manage applications remotely. This eliminates the need for frequent physical visits to server rooms, especially those geographically dispersed.
Many remote monitoring and management (RMM) platforms integrate RDP functionality. This allows IT service providers to efficiently manage numerous client machines from a central console, providing proactive support and quick responses to incidents across their customer base.
Managing Servers and Systems
System administrators frequently rely on RDP for managing Windows servers. Whether servers are located on-premises in a server closet or hosted in a cloud environment like Microsoft Azure or AWS, RDP provides essential graphical access for administrative tasks that require a GUI.
Tasks such as installing server roles (like Active Directory or IIS web server), configuring complex applications, managing user accounts graphically, or reviewing event logs are often easier through an RDP session than command-line interfaces alone, especially for administrators accustomed to graphical tools.
Cloud providers often supply pre-configured virtual machines with RDP enabled by default (though secured with strong credentials). Administrators connect using an RDP client to set up, configure, and maintain these cloud-based servers just as they would physical servers in their own data center.
While command-line tools like PowerShell and SSH (Secure Shell, primarily for Linux/Unix) are powerful for automation and specific tasks, RDP remains crucial for managing the full graphical environment of Windows Server operating systems. It provides a complete remote desktop experience necessary for many management workflows.
This remote management capability ensures that administrators can maintain server health, security, and performance from anywhere with a network connection. This flexibility is vital for ensuring business continuity and responding promptly to server-related issues, regardless of the administrator’s location.
Is RDP Secure? Key Features & Basic Safety Tips
RDP includes several built-in security features, but its overall security depends heavily on proper configuration and user practices. While the protocol itself offers encryption and authentication mechanisms, vulnerabilities can arise if it’s not set up and used carefully, making it a target for cyberattacks.
Understanding both the inherent security features and potential risks is crucial. Let’s look at key security aspects like encryption and Network Level Authentication (NLA), along with essential safety tips to minimize risks when using Remote Desktop Protocol.
Built-in Security: Encryption
RDP encrypts the data transmitted between the client and server. This means the information, including screen data, keystrokes, and mouse movements, is scrambled during transit. Encryption prevents unauthorized parties from easily eavesdropping on the connection if they intercept the network traffic.
By default, RDP attempts to negotiate the highest level of encryption supported by both the client and the server, typically using strong algorithms like 128-bit RC4 or AES (Advanced Encryption Standard). This ensures confidentiality for the data exchanged during the remote session.
While encryption protects data in transit, it doesn’t protect against other threats like compromised credentials or vulnerabilities in the RDP software itself. Therefore, encryption is a necessary but not sufficient security measure on its own; it must be part of a broader security strategy.
Think of encryption like sending a message in a secret code. Even if someone intercepts the message (the network traffic), they can’t read its contents without the key to decipher the code. This protects the confidentiality of your remote session data as it travels across potentially insecure networks like the internet.
What is Network Level Authentication (NLA)?
Network Level Authentication (NLA) is a security feature that requires user authentication before establishing a full RDP session. Introduced in later versions of RDP, NLA adds an extra layer of protection compared to older methods where the full session started before login.
With NLA enabled, the RDP client must first authenticate the user to the server (usually using their Windows login credentials) before the Windows login screen is even displayed remotely. This process consumes fewer server resources for unauthenticated connection attempts.
The primary benefit of NLA is mitigating denial-of-service (DoS) attacks and reducing exposure to brute-force password attacks. Since authentication happens early, malicious actors can’t easily tie up server resources by initiating numerous RDP sessions just to reach the login prompt.
Microsoft strongly recommends enabling NLA on RDP servers whenever possible. It significantly enhances security by ensuring only authenticated users can initiate sessions. Most modern Windows operating systems support and often enable NLA by default for RDP connections.
Imagine NLA as a security checkpoint before you even reach the main entrance (the login screen) of a building (the remote server). You must present valid credentials at this initial checkpoint to proceed further, preventing unauthorized individuals from even getting close to the entrance.
Quick Tips for Staying Safer with RDP
While RDP has security features, proactive measures are essential for safe usage. One of the most critical steps is using strong, unique passwords for accounts allowed RDP access. Weak or reused passwords are prime targets for brute-force attacks aiming to guess credentials.
Change the default RDP port (3389) to a non-standard port. While not foolproof (security through obscurity), this simple step can deter many automated scanning tools that specifically look for open port 3389. Remember to update firewall rules accordingly if you change the port.
Enable Network Level Authentication (NLA) on the RDP server. As discussed, this provides crucial pre-authentication, significantly reducing the attack surface. Ensure both client and server support NLA for it to function correctly. Check this setting in your System Properties under the Remote tab.
Limit who can connect via RDP. Use the principle of least privilege. Only grant RDP access permissions to users who absolutely need it. Avoid using administrator accounts for routine RDP access whenever possible. Configure permissions carefully through Remote Desktop Users groups.
Keep your operating systems (both client and server) and RDP client software fully updated. Microsoft regularly releases security patches to fix known vulnerabilities in RDP and Windows. Promptly applying these updates is vital to protect against exploits targeting these flaws.
Use a Virtual Private Network (VPN) for RDP connections, especially over the internet. A VPN creates an additional encrypted tunnel for your RDP traffic, adding another layer of security and hiding the RDP server from direct exposure to the public internet.
Implement account lockout policies. Configure Windows to automatically lock an account after a certain number of failed login attempts (e.g., 5 attempts). This effectively thwarts brute-force attacks trying thousands of password combinations against user accounts via RDP.
Monitor RDP logs regularly. Windows event logs track successful and failed RDP login attempts. Reviewing these logs can help detect suspicious activity, such as repeated failed logins from unknown IP addresses, indicating potential attack attempts that require investigation.
Consider using an RDP Gateway. For larger environments, an RDP Gateway (now often part of Remote Desktop Services) acts as a secure entry point. It allows authorized remote users to connect to specific internal network resources without exposing the RDP servers directly to the internet.
Educate users about RDP security. Ensure anyone using RDP understands the risks, the importance of strong passwords, and the need to report suspicious activity. Human awareness is a critical component of any security strategy, complementing technical controls effectively. NordLayer research suggests RDP is frequently targeted in cyberattacks, emphasizing the need for robust security.
Using RDP: Windows, Mac, Linux, and More
Remote Desktop Protocol, being a Microsoft technology, has its roots deeply embedded in the Windows ecosystem. However, its usefulness has led to the development of client applications for various other operating systems, making remote connections possible from a wide range of devices.
Built Right into Windows
RDP server functionality is natively integrated into Professional, Enterprise, and Server editions of Microsoft Windows. This means these versions can host incoming RDP connections without needing additional software installation. Home editions of Windows typically only include the RDP client, not the server capabilities.
To enable incoming RDP connections on a supported Windows version, you usually go to System Properties, select the “Remote” tab, and enable “Allow remote connections to this computer.” It’s also here you’d typically ensure the “Allow connections only from computers running Remote Desktop with Network Level Authentication” box is checked for better security.
The built-in RDP client application in Windows is called Remote Desktop Connection. You can usually find it by searching for “Remote Desktop” or “mstsc.exe” (its executable file name) in the Windows search bar. This client allows you to initiate outgoing connections to RDP servers.
This native integration makes setting up basic RDP connections between Windows machines relatively straightforward, contributing significantly to its widespread use within corporate environments and by individuals needing to access Windows PCs remotely. No third-party licenses are usually needed for basic peer-to-peer connections.
Connecting from Other Devices
Microsoft provides official Remote Desktop client applications for non-Windows platforms. These free apps allow users on macOS, iOS (iPhone/iPad), and Android devices to connect to Windows PCs or servers running the RDP server service. These clients aim to provide a consistent experience across platforms.
For macOS users, the “Microsoft Remote Desktop” app is available from the Mac App Store. It allows connection to RDP servers, supporting features like NLA, multiple monitors, and redirection of local folders or printers, providing a rich remote Windows experience on a Mac.
Similarly, apps for iOS and Android are available through their respective app stores (Apple App Store and Google Play Store). These mobile clients enable connecting to remote Windows desktops from tablets and smartphones, useful for quick access or management tasks on the go.
For Linux users, while there isn’t an official Microsoft RDP client, several excellent open-source and third-party options exist. Popular choices include Remmina, FreeRDP (often used as a backend library by other clients), Vinagre, and KRDC. These clients typically support the core RDP features, including NLA.
This cross-platform client availability means you aren’t limited to using Windows to connect to a Windows machine via RDP. You can initiate secure remote sessions from virtually any major operating system, enhancing the flexibility and reach of Remote Desktop Protocol for diverse user environments.
(Optional but Recommended) RDP vs. Other Remote Tools (Like VNC/TeamViewer)
While RDP is a powerful and widely used protocol, it’s not the only option for remote desktop access. Understanding how it compares to other popular tools like VNC (Virtual Network Computing) and commercial products like TeamViewer can help clarify its specific strengths and use cases.
RDP primarily works by transmitting drawing commands and graphical primitives. It leverages the remote machine’s graphics processing capabilities. In contrast, VNC fundamentally works by sending compressed pixel data representing the remote screen’s framebuffer. This difference can impact performance depending on network conditions and content type.
VNC is platform-independent by design, with various client and server implementations available across Windows, macOS, Linux, and more (e.g., RealVNC, TightVNC, UltraVNC). RDP server capability is predominantly tied to Windows, although RDP clients are widely available. RDP often feels more responsive, especially over higher latency networks.
Commercial tools like TeamViewer, AnyDesk, or Splashtop offer an all-in-one solution. They typically handle firewall traversal and NAT (Network Address Translation) issues automatically, making setup easier for non-technical users. They often bundle features like file transfer, chat, and session recording into a single application.
These commercial solutions often use proprietary protocols optimized for performance and ease of use. However, they usually require installing their software on both the client and server machines and often involve subscription fees for commercial use, unlike the basic RDP functionality built into Windows Pro/Enterprise.
RDP’s strength lies in its native Windows integration, robust performance (especially within Windows environments), and inclusion in Windows licenses. Tools like TeamViewer excel in ease of setup across platforms and firewalls. VNC offers broad platform compatibility, often favored in mixed OS environments or for specific technical needs.
Choosing between them depends on factors like operating systems involved, technical expertise, budget, required features, and specific security needs. For accessing Windows machines, especially within a corporate network or with proper security configurations (like VPNs), RDP remains a very strong contender.
Wrapping Up: Your RDP Basics
So, we’ve journeyed through the world of Remote Desktop Protocol. Let’s quickly recap the essentials you’ve learned. RDP is Microsoft’s technology allowing you to securely view and control another computer over a network connection, making remote access feel local.
It operates on a client-server model, where your local device (client) connects to the remote machine (server), typically using network port 3389. Your inputs (keyboard, mouse) are sent to the server, and its screen display is sent back to you, all managed by the RDP rules.
RDP is incredibly useful for remote work, IT support, and server administration, enabling access to resources and systems from virtually anywhere. Its native integration into professional versions of Windows makes it a convenient and common choice within that ecosystem.
Security is crucial with RDP. While features like encryption and Network Level Authentication (NLA) provide baseline protection, safe usage demands strong passwords, regular updates, limited access permissions, and potentially using VPNs or RDP Gateways, especially for internet-facing connections.
While alternatives like VNC and TeamViewer exist, RDP’s integration with Windows and performance characteristics make it a powerful tool. With clients available for Mac, Linux, iOS, and Android, you can connect to your remote Windows systems from almost any device. Understanding RDP empowers you to leverage remote access effectively and securely.
