Have you ever wondered how files travel across the internet? Perhaps you need to upload files to your website or download data from a server. One of the original methods for this is the File Transfer Protocol, commonly known as FTP. It’s a fundamental technology worth understanding.
FTP stands for File Transfer Protocol. It is a standard set of rules computers use to transfer files from one system to another over a network, like the internet. Think of it as a digital delivery service specifically designed for moving files between computers, using a client and a server.
This guide will walk you through exactly what FTP is. We will explore how it works, its common uses, and critically, discuss its security limitations. You will also learn about the modern, secure alternatives that are essential for protecting your data in today’s online world. Let’s dive in.
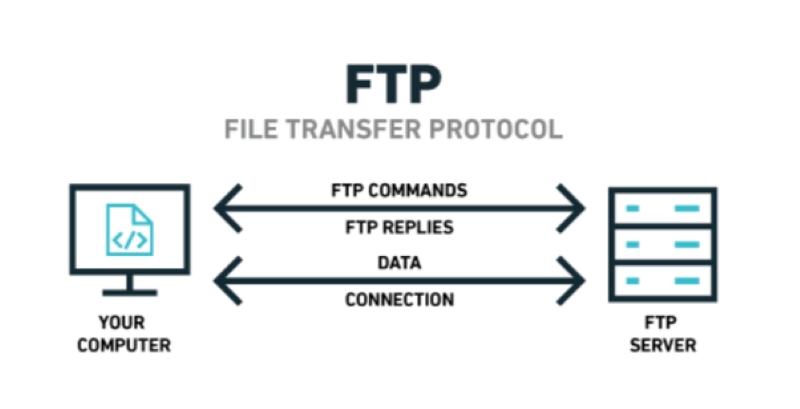
How Does FTP Work? Understanding the Core Mechanics
At its heart, FTP operates using a client-server architecture. This means two computer programs interact to make the file transfer happen. One program acts as the client, requesting actions, while the other is the server, responding to those requests and providing access to files.
The FTP Client-Server Architecture Explained
The FTP client is the software you interact with directly on your local computer. Popular examples include FileZilla, WinSCP, and Cyberduck. This client software sends your commands, like “upload this file” or “list available files,” to the FTP server, acting as your agent in the transfer process.
The FTP server is software running on a remote computer, often a powerful machine hosting websites or storing data. Its job is to constantly listen for connection requests from FTP clients. When a client connects, the server manages authentication (checking login details) and handles file access requests.
Imagine the server as a secure warehouse for files. The client is like a trusted courier you send with specific instructions. The client arrives at the warehouse, presents credentials, requests certain packages (files), and either delivers new ones or picks up existing ones based on your commands.
To start, your FTP client initiates contact with the FTP server using its address (like ftp.example.com or an IP address). The server responds, beginning a conversation. The client then usually needs to provide a username and password to gain access before any file operations can begin.
Understanding FTP Connections: Control and Data Channels
A unique aspect of FTP is that it uses two distinct communication channels, or connections, between the client and the server. This separation handles commands differently from the actual file data being transferred. Think of it as having one phone line for instructions and another for sending the package itself.
The first channel is the Control Connection. Typically established on the server’s port 21, this connection handles all the commands you send (like USER for username, PASS for password, LIST for directory contents) and the server’s responses. This connection stays active throughout your entire FTP session.
Importantly, on standard FTP, the commands and responses sent over the control connection are usually in plain text. This includes your username and password, which is a major security concern we will discuss later. It’s like shouting instructions and login details across a crowded room.
The second channel is the Data Connection. This connection is opened only when files are actually being transferred (uploaded or downloaded) or when a directory listing is requested. Unlike the control connection, it’s temporary and closes once the data transfer is complete. How it opens depends on the mode: Active or Passive.
Both these connections rely on the underlying TCP/IP (Transmission Control Protocol/Internet Protocol) suite. TCP ensures reliable, ordered data delivery for both commands and files, while IP handles addressing the data packets to the correct client or server across the network. FTP builds its rules on top of this foundation.
Active Mode vs. Passive Mode FTP Explained
How the temporary Data Connection gets established leads to two distinct operational modes: Active FTP and Passive FTP. Choosing the right mode is often crucial for successfully connecting, especially when firewalls are involved. Understanding the difference helps troubleshoot common connection problems you might encounter.
In Active Mode, the client first tells the server which port number it (the client) is listening on for the data connection. The server then initiates the data connection back to the client’s specified port. The server typically sends this data connection request from its own port 20.
The challenge with Active Mode arises with client-side firewalls or Network Address Translation (NAT) devices (like home routers). These often block incoming connection attempts from unknown external sources (like the FTP server trying to connect back). This blockage prevents the data connection, causing transfers or listings to fail.
For example, if your home computer running an FTP client is behind a router, the router might block the server’s attempt to connect back for the data transfer in Active Mode. The client sends the PORT command, but the server’s connection attempt from port 20 gets dropped by the router.
To overcome this common issue, Passive Mode (PASV) was developed. In this mode, the client asks the server to enter passive mode using the PASV command. The server then opens a high-numbered port (above 1023) on its end and tells the client which port number to connect to.
Crucially, in Passive Mode, the client initiates the data connection to the server’s specified temporary port. Since the connection originates from the client side, it usually passes through client-side firewalls and NAT devices without being blocked. This makes Passive Mode the generally preferred and more reliable option today.
Imagine Active mode is like telling the mailroom “I’m at desk 5, send the package here.” But the building security (firewall) stops the delivery person. Passive mode is like asking the mailroom “Where should I pick up the package?” and they reply “Go to loading dock 7,” which security allows you to access.
Most modern FTP client software allows you to select between Active and Passive mode, often defaulting to Passive due to its better compatibility with typical network setups. If you experience connection timeouts specifically when trying to list directories or transfer files, switching modes is a common troubleshooting step.
File Transfer Modes: ASCII vs. Binary
FTP also defines two modes for transferring the file data itself: ASCII mode and Binary mode. Choosing the wrong mode can lead to corrupted files, especially when transferring between different operating systems (like Windows and Linux/macOS). Knowing when to use each is important for data integrity.
ASCII Mode is designed specifically for transferring plain text files (like .txt, .html, .css, .js files). Its key function is to automatically handle differences in how various operating systems mark the end of a line. Windows uses carriage return and line feed (CRLF), while Unix-based systems use just line feed (LF).
When transferring a text file in ASCII mode, FTP can convert these line endings appropriately between the client and server systems. However, if you mistakenly use ASCII mode to transfer a non-text file (like an image, a Zip archive, or an executable program), this conversion process will corrupt the file’s data structure.
Binary Mode, on the other hand, transfers the file byte-by-byte exactly as it is, without any interpretation or modification. This is essential for all non-text files – images (.jpg, .png), videos (.mp4), compressed archives (.zip, .gz), software executables (.exe, .dmg), and documents like PDFs.
Because Binary mode makes no changes, it’s generally the safer default mode to use for all transfers unless you are absolutely certain you are transferring a plain text file and need line-ending conversion. Using Binary mode for a text file usually causes no harm, making it a robust choice.
Most FTP clients allow you to set the transfer mode, with many defaulting to “Auto” mode. In Auto mode, the client attempts to guess the correct mode based on the file extension. While convenient, explicitly setting Binary mode often prevents unexpected file corruption issues, particularly for beginners.

What Was FTP Used For? Common Use Cases
FTP became popular because it addressed a fundamental need: moving files reliably between networked computers. While newer technologies have emerged, understanding its original use cases provides context for its design and limitations. It was a workhorse protocol for many years in several key areas.
One of the most common historical uses was Website Development and Management. Developers would create website files (HTML pages, CSS stylesheets, JavaScript code, images) on their local computers. They then used an FTP client to upload these files to the web hosting server, making the website live.
Server Administration also frequently involved FTP. System administrators might use FTP to upload new configuration files to a server or, more commonly, to download log files from the server back to their local machine for analysis and troubleshooting. It provided a standard way to access the server’s file system remotely.
Before the rise of cloud storage services like Dropbox or Google Drive, FTP was a common method for Sharing Large Files. If a file was too large for email attachments, users could upload it to an FTP server, and the recipient could then download it using an FTP client.
Some organizations used FTP for Simple Backups. Automated scripts could be set up to connect to an FTP server and upload copies of important files or directories on a regular schedule. While basic, it provided a mechanism for offsite storage, though versioning and security were often minimal.
Finally, Anonymous FTP allowed servers to offer files publicly without requiring individual user accounts. Users could log in with a generic username like “anonymous” or “ftp” (often providing their email as a password). This was used for distributing software, technical documents, or research data widely.
While some of these uses persist, especially in legacy systems or specific technical contexts, many have been replaced. Website deployment now often uses more integrated tools or secure protocols like SFTP. Cloud services dominate large file sharing. However, the concept of transferring files remains crucial.
The Critical Security Warning: Is Standard FTP Safe?
Now we arrive at the most critical point for anyone considering using FTP today: Standard FTP is fundamentally insecure when used over untrusted networks like the internet. Its original design predates modern cybersecurity concerns, leaving it dangerously vulnerable. You must understand these risks.
Why Standard FTP is Not Secure
The primary reason standard FTP is unsafe is its complete lack of encryption. When you connect to an FTP server, your username, your password, all commands you issue, and all data you transfer are sent across the network as plain text. This means anyone monitoring the network traffic can easily read it.
Imagine logging into your bank account, but shouting your username and password across a public space – that’s analogous to using standard FTP over the internet. Anyone “listening” on the network path (e.g., on the same public Wi-Fi, or via compromised network equipment) can capture your credentials using tools called packet sniffers.
Beyond credential theft, the lack of data integrity checks is another significant flaw. Standard FTP doesn’t inherently verify that the file received is exactly the same as the file sent. This opens the door for potential Man-in-the-Middle (MitM) attacks, where an attacker could intercept and alter files during transit without your knowledge.
Furthermore, FTP servers themselves can be targets. Attackers might try brute-force attacks, repeatedly guessing usernames and passwords to gain unauthorized access. Older FTP server software might also have specific vulnerabilities that could be exploited to compromise the server or access restricted files.
These security failings are not minor inconveniences; they represent serious risks to data confidentiality, integrity, and system security. Using standard FTP for sensitive information or over public networks is strongly discouraged by virtually all modern security standards and practices. Its use introduces unacceptable vulnerabilities.
Extremely Limited Safe Scenarios (Use With Caution)
Given the severe risks, are there any situations where standard FTP might be acceptable? The scenarios are extremely limited and require careful consideration. Primarily, it might be deemed usable only within a completely private, trusted network where the risk of interception is considered negligible.
For example, transferring non-sensitive files between two machines on your own isolated home network might be acceptable, although even then, enabling encryption is always better practice. Relying on the network itself being “safe” is a risky assumption that can change unexpectedly.
Another edge case involves Anonymous FTP for accessing purely public, non-sensitive data. If a server is specifically set up for public distribution and requires no login (or only the generic “anonymous” login), the risk of credential theft is removed. However, data integrity issues could still potentially exist.
Even in these limited cases, caution is paramount. The vast majority of file transfers, especially those involving login credentials or potentially sensitive data, and any transfer occurring over the public internet, should absolutely not use standard, unencrypted FTP. The risks are simply too high.
Secure File Transfer Protocols: Meet SFTP and FTPS
Fortunately, the severe security shortcomings of standard FTP were recognized long ago, leading to the development of secure alternatives. These protocols provide the necessary encryption and protection for modern file transfers. The two main secure options you need to know are FTPS and SFTP.
It’s crucial to understand that relying on standard FTP today is like sending valuable documents via postcard – easily read by anyone along the way. Using FTPS or SFTP is like using a secure, tracked, and sealed courier service, ensuring your data arrives safely and privately.
FTPS: Adding Security via SSL/TLS
FTPS (FTP over SSL/TLS) works by adding a layer of cryptographic security using the Secure Sockets Layer (SSL) or, more commonly today, its successor, Transport Layer Security (TLS). This is the same encryption technology that secures websites when you see https in your browser address bar.
FTPS essentially wraps the standard FTP communication (both control and data connections) inside an encrypted tunnel. This prevents eavesdropping on credentials and file contents. It comes in two main flavors regarding how the secure connection is initiated.
Implicit FTPS requires clients to establish an SSL/TLS connection immediately upon connecting to the FTPS server, usually on a dedicated port like 990. Explicit FTPS (also known as AUTH TLS or FTPES) starts as a standard FTP connection on port 21, and the client then explicitly requests encryption using commands like AUTH TLS. Explicit FTPS is more common.
While FTPS leverages familiar FTP commands and structures, its use of multiple ports (one for control, another potentially dynamic one for data) can sometimes make configuring firewalls more complex compared to SFTP. However, it provides robust encryption for traditional FTP workflows.
SFTP: Security Through SSH
SFTP stands for SSH File Transfer Protocol. Despite the similar name, it’s technically not FTP with SSH layered on top. It’s a completely different protocol designed from the ground up as a subsystem of SSH (Secure Shell), a widely used protocol for secure remote login and command execution.
SFTP runs entirely over a single, secure SSH connection, typically established on port 22. All aspects – authentication, commands, and data transfer – happen within this encrypted SSH tunnel. This single-port operation significantly simplifies firewall configuration compared to FTPS or Active Mode FTP.
Beyond robust encryption, SFTP often supports more advanced authentication methods inherited from SSH, such as using public key cryptography instead of just passwords. This provides an even higher level of security against brute-force attacks. Many server administrators and developers prefer SFTP for its security and robustness.
Because it’s a different protocol, SFTP commands are not identical to FTP commands, although modern GUI clients often abstract these differences away, providing a similar user experience for both protocols. The key takeaway is that SFTP offers strong security via the well-established SSH protocol.
Quick Comparison: FTP vs. FTPS vs. SFTP
Let’s summarize the key differences in a way that’s easy to grasp:
- FTP: The original protocol. Insecure (plain text credentials and data). Uses Port 21 (control) and Port 20/dynamic (data).
- FTPS: Standard FTP + SSL/TLS Encryption. Secure. Uses Port 21 (explicit control) or 990 (implicit), plus data ports. Can be tricky with firewalls.
- SFTP: Different protocol using SSH Encryption. Secure. Uses a single port (usually 22) for everything. Often preferred for simplicity and robustness.
When choosing a protocol for transferring files today, especially over the internet, always prioritize SFTP or FTPS over standard FTP. SFTP is frequently recommended due to its single-port operation and strong security foundation in SSH.
FTP’s Origins: A Brief History Lesson
To fully appreciate why FTP works the way it does (including its security limitations), it helps to understand its history. FTP is one of the internet’s oldest protocols, predating even the World Wide Web and email as we know them today. Its origins trace back to the early days of computer networking.
The first specification for FTP was written by Abhay Bhushan at MIT in 1971 (RFC 114) for use on the ARPANET, the precursor network to the modern internet. The goal was simply to enable file sharing between the limited number of research computers connected at the time. Security wasn’t the primary focus then.
Over the years, FTP underwent several revisions to add features and refine its operation. The most significant defining standard still referenced today is RFC 959, published by the Internet Engineering Task Force (IETF) in 1985. This document solidified the client-server model, control/data connections, and commands still recognizable in FTP.
FTP’s longevity highlights its success in solving a fundamental problem. It established key concepts used by many later protocols. However, the internet environment has drastically changed since 1985. The lack of built-in security, acceptable then, became a critical flaw as the internet grew public and commercial.
Understanding this history explains why standard FTP operates in plain text – it was designed for a smaller, more trusted network environment. It also underscores why modern protocols like SFTP and FTPS were necessary developments to adapt file transfer for the security demands of today’s interconnected world.
Conclusion: FTP’s Legacy and Today’s Best Practices
So, what is File Transfer Protocol (FTP)? It’s a foundational network protocol designed for transferring files between a client and a server. It uses separate connections for commands and data and relies on a client-server interaction model that influenced many subsequent internet technologies.
However, the most crucial takeaway is that standard FTP is inherently insecure. It transmits credentials and data in plain text, making it unsuitable for use over the internet or any untrusted network. Continuing to use standard FTP for sensitive operations exposes you to significant security risks like data theft and unauthorized access.
Therefore, the clear recommendation and modern best practice is to always use secure alternatives like SFTP (SSH File Transfer Protocol) or FTPS (FTP over SSL/TLS) whenever you need to transfer files. SFTP, running over SSH on a single port, is often favored for its robustness and ease of firewall management.
While understanding FTP provides valuable historical context and insight into networking fundamentals, its practical use should be limited to specific legacy scenarios or replaced entirely by its secure successors. Prioritize security: choose SFTP or FTPS to protect your files and credentials in transit.
