Ever seen that padlock icon in your browser or heard about “end-to-end encryption” and wondered what it all means? Encryption sounds complex, but it’s a fundamental concept for keeping information safe in our digital world. This guide will break down what encryption is in simple, easy-to-understand terms, explain how it works without getting too technical, and show you why it’s so important for protecting your online privacy and data security every day.
What is Encryption in Simple Terms?
At its core, encryption transforms your readable data, called plaintext, into an unreadable format known as ciphertext. Think of plaintext as a normal message anyone can read. Ciphertext is that same message scrambled into a secret code only authorized individuals can decipher.
Imagine writing a secret message to a friend using a special codebook only you two share. Encryption works similarly for digital information. The original message is the plaintext. The coded message is the ciphertext. The codebook represents the method and key used.
This conversion process makes sensitive information useless to anyone who might intercept it without permission. If hackers steal encrypted data, they only get scrambled nonsense. They cannot understand the original information without the secret key needed to unlock it, ensuring your data remains confidential.

Why is Encryption So Important Today?
Encryption is crucial because it protects our digital lives. It safeguards sensitive information from falling into the wrong hands, ensuring privacy and confidentiality. In an era of frequent data breaches and online threats, encryption provides a vital layer of defense for individuals and organizations alike.
Without encryption, online activities like banking, shopping, or private messaging would be incredibly risky. Your personal details, financial information, and private conversations could be easily exposed. Encryption makes these everyday digital interactions significantly safer by scrambling the underlying data exchanged across networks.
Furthermore, many industries are legally required to use encryption. Regulations like the General Data Protection Regulation (GDPR) in Europe and the Health Insurance Portability and Accountability Act (HIPAA) in the US mandate encryption. This protects sensitive customer and patient data, avoiding hefty fines and reputational damage.
Protecting Your Personal Privacy Online
Every day, we share vast amounts of personal information online. Encryption helps keep this information private. It protects your emails, messages, Browse history, and personal files. This prevents advertisers, hackers, or other snoops from easily accessing your private digital footprint and conversations.
Consider end-to-end encrypted messaging apps like Signal or WhatsApp. Only you and the person you’re communicating with can read the messages. Even the company providing the service cannot decipher your conversations. This level of privacy is only possible thanks to strong encryption techniques.
Similarly, when you browse secure websites (those starting with HTTPS), encryption protects the data exchanged between your browser and the site. This includes login details, personal information entered into forms, and Browse activity. It shields your online actions from eavesdroppers on the network.
Keeping Sensitive Data Secure from Hackers
Data breaches are a constant threat, potentially exposing sensitive information like credit card numbers, bank details, passwords, and personal identification. Encryption renders stolen data useless to attackers because they cannot read it without the decryption key, ensuring data confidentiality.
Imagine a company storing customer payment details. If their database is hacked, unencrypted data would be a goldmine for criminals. However, if the data is strongly encrypted, the hackers obtain only meaningless ciphertext. This significantly mitigates the damage caused by a security breach.
This protection applies to data stored on devices too. Encrypting your laptop’s hard drive or your smartphone means that if the device is lost or stolen, the thief cannot access your personal files, photos, or account information without your password or key.
Building Trust and Meeting Security Standards
For businesses, using encryption is essential for building customer trust. When customers know their data is protected, they feel more confident interacting with the company online. Demonstrating strong security practices, including robust encryption, becomes a competitive advantage and fosters loyalty.
Meeting industry-specific security standards often mandates encryption. For example, the Payment Card Industry Data Security Standard (PCI DSS) requires encryption for credit card data. Compliance isn’t just about avoiding penalties; it shows a commitment to protecting stakeholders and maintaining operational integrity.
Organizations use encryption to protect internal communications, trade secrets, and sensitive research data. It safeguards intellectual property and ensures business continuity. Implementing strong encryption protocols is a hallmark of a mature and responsible cybersecurity posture, reassuring partners and investors.
How Does Encryption Actually Work?
Encryption works through a defined process involving specific components. It uses a mathematical recipe called an algorithm and a secret value called a key to transform readable plaintext into unreadable ciphertext. Understanding these basic steps helps demystify how your data gets protected digitally.
The process begins with the original data you want to protect (plaintext). This data is fed into the encryption algorithm. The algorithm, guided by the unique encryption key, performs complex mathematical operations on the data, effectively scrambling it thoroughly according to the defined rules.
The result is ciphertext – the encrypted version of your data. This ciphertext appears as random gibberish to anyone without the correct key. To revert it back to readable plaintext, a corresponding decryption process using the right key is required. This ensures only authorized parties can access the information.
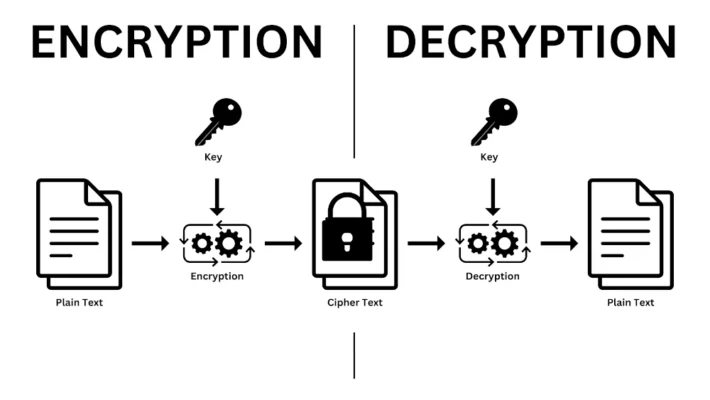
From Readable Data (Plaintext) to Secret Code (Ciphertext)
Let’s clarify the core terms. Plaintext is simply any information in its original, understandable form. This could be an email message, a document, a password, or any piece of digital data before it undergoes the encryption process. It’s human-readable or machine-readable data.
Ciphertext, on the other hand, is the result of applying encryption to plaintext. It’s the scrambled, seemingly random sequence of characters or bits that represents the original data in its protected state. Ciphertext is intentionally designed to be unintelligible without the appropriate decryption key.
The fundamental goal of encryption is this transformation from plaintext to ciphertext. This change ensures that even if the data falls into unauthorized hands during storage or transmission, its meaning remains hidden, preserving confidentiality and security against eavesdropping or theft.
The Role of Encryption Algorithms
An encryption algorithm, sometimes called a cipher, is the specific mathematical formula or set of rules used to perform the encryption and decryption. Think of it as the detailed instructions for scrambling and unscrambling the data. Different algorithms offer varying levels of security and efficiency.
These algorithms are publicly known and standardized. Their security doesn’t rely on keeping the method secret, but rather on the complexity of the mathematical problems they employ. Examples include AES (Advanced Encryption Standard) and RSA (Rivest–Shamir–Adleman), which we’ll discuss later.
The algorithm dictates how the key interacts with the plaintext to produce ciphertext. A strong algorithm ensures that there are no shortcuts to reversing the process without the key. Standards bodies like NIST (National Institute of Standards and Technology) evaluate and approve algorithms for widespread use.
The Magic Ingredient: Encryption Keys
If the algorithm is the recipe, the encryption key is the secret ingredient that makes each encryption unique. A key is typically a string of numbers or characters generated for a specific purpose. It’s used by the algorithm to customize the scrambling process.
Without the correct key, even knowing the algorithm used is generally insufficient to decrypt the ciphertext efficiently. The security of most modern encryption relies heavily on keeping the key secret (in symmetric encryption) or protecting the private key (in asymmetric encryption).
Key length is important – longer keys generally offer more possible combinations, making them harder for attackers to guess via brute-force attacks (trying every possible key). Common key lengths today might be 128, 192, or 256 bits for symmetric keys, and 2048 bits or more for asymmetric keys.
Unlocking the Code: What is Decryption Explained?
Decryption is the process of converting ciphertext back into its original, readable plaintext form. It is essentially the reverse of encryption. To perform decryption successfully, you typically need the correct decryption key and the corresponding decryption algorithm (usually the inverse of the encryption algorithm).
When an authorized recipient receives encrypted data (ciphertext), they use their decryption key. The decryption algorithm applies this key to the ciphertext, reversing the mathematical operations performed during encryption. This unscrambles the data, restoring the original plaintext message or file accurately.
If the wrong key is used, the decryption process will fail, resulting in either an error or more garbled data. This ensures that only individuals possessing the correct key can access the information, completing the security cycle initiated by encryption.
What Are the Main Types of Encryption?
There are two primary types of encryption methods used today: Symmetric Encryption and Asymmetric Encryption. They differ mainly in how they handle the keys used for encrypting and decrypting information. Understanding this distinction is key to grasping how different security systems work.
Symmetric encryption uses a single, shared secret key for both locking (encrypting) and unlocking (decrypting) data. Asymmetric encryption, also known as public-key cryptography, uses a pair of keys: one public key for encrypting and a separate private key for decrypting. Each type has its strengths and use cases.
Choosing between symmetric and asymmetric encryption often depends on the specific application. Factors include the need for speed, the complexity of managing keys, and whether the communicating parties can securely share a secret key beforehand. Many systems use a combination of both methods.
Symmetric Encryption: Using a Shared Secret Key
Symmetric encryption algorithms use the exact same secret key to both encrypt plaintext and decrypt ciphertext. This means the sender and receiver must securely share this single key before they can communicate privately. It’s like having two identical keys to the same padlock.
This method is generally faster and less computationally intensive than asymmetric encryption. This makes it well-suited for encrypting large amounts of data, such as entire files, databases, or streaming video. Its main challenge lies in securely distributing and managing the shared secret key.
Common examples of well-regarded symmetric algorithms include AES (Advanced Encryption Standard), which is widely used globally for securing sensitive data. Older standards like DES (Data Encryption Standard) and Triple DES (3DES) also fall into this category but are less secure than modern AES implementations.
Asymmetric Encryption: The Public & Private Key Pair
Asymmetric encryption, or public-key cryptography, uses two mathematically linked keys: a public key and a private key. The public key can be shared freely without compromising security. It is used to encrypt data or verify a digital signature. The private key must be kept secret by the owner.
Data encrypted with a user’s public key can only be decrypted using their corresponding private key. This solves the key distribution problem inherent in symmetric encryption. You don’t need a pre-shared secret. It’s like having a mailbox with a public slot (anyone can drop a message in) but only you have the private key to open it.
While generally slower than symmetric encryption, asymmetric methods are fundamental for secure key exchange, digital signatures, and initial handshakes in protocols like TLS/SSL (which secures HTTPS). RSA is one of the most well-known and widely used asymmetric algorithms for these purposes.
Where Do You Encounter Encryption?
You interact with encryption constantly in your daily digital life, often without realizing it. Encryption works behind the scenes to secure your web Browse, messaging, Wi-Fi connections, stored files, and much more. Recognizing these examples helps appreciate its practical importance.
From the moment you connect to a secure website to sending a private message or saving a file, encryption technologies are likely involved. These systems automatically protect your data confidentiality and integrity across various platforms and devices, making the digital world safer to navigate.
Let’s look at some specific, common examples where encryption plays a vital role. Understanding these applications makes the concept less abstract and highlights how integral it is to modern technology and online security practices, protecting billions of users daily.
Secure Websites (HTTPS and the Padlock Icon)
When you visit a website and see https:// at the beginning of the address and a padlock icon in your browser bar, it means your connection is encrypted. This protocol, HTTPS (Hypertext Transfer Protocol Secure), uses TLS (Transport Layer Security) or its predecessor SSL (Secure Sockets Layer) encryption.
This encrypts the data exchanged between your web browser and the website’s server. It protects sensitive information like login credentials, credit card numbers entered during online shopping, and personal details submitted through forms. It prevents eavesdroppers on the network from spying on your activity.
Website encryption relies heavily on asymmetric cryptography (like RSA) to securely exchange a symmetric key during the initial connection handshake. Then, the faster symmetric encryption (like AES) is used to encrypt the actual bulk data transferred during your Browse session, combining speed and security.
Encrypted Messaging Apps
Many popular messaging apps now feature end-to-end encryption (E2EE). This means messages are encrypted on the sender’s device and can only be decrypted by the intended recipient’s device. No one in between – not even the app provider – can read the message content.
Apps like Signal and WhatsApp use protocols like the Signal Protocol to implement strong E2EE. This ensures your private conversations, photos, and videos shared within the app remain confidential. It provides a high level of privacy for personal communications against interception or surveillance.
This type of encryption typically uses asymmetric keys to establish a secure session and verify identities initially. Then, unique symmetric keys are generated for each conversation or message, ensuring ongoing confidentiality and message integrity between the communicating parties only.
Protecting Your Home Wi-Fi Network (WPA2/WPA3)
When you connect your devices to your home Wi-Fi network, encryption secures the wireless communication. Modern routers use security protocols like WPA2 (Wi-Fi Protected Access 2) or the newer, more secure WPA3. These protocols encrypt the data transmitted between your devices and the router.
This encryption prevents neighbors or anyone nearby from easily intercepting your internet traffic or gaining unauthorized access to your network. It ensures that your online activities conducted over Wi-Fi remain private and secure within your home environment. Always use a strong password for your Wi-Fi network.
WPA2 and WPA3 primarily use symmetric encryption algorithms like AES to protect the confidentiality of the wireless data packets. Establishing the initial secure connection often involves a handshake process (like the WPA3 Simultaneous Authentication of Equals – SAE) to securely derive the shared encryption keys.
Keeping Files Safe on Your Devices (Disk & File Encryption)
Encryption can protect data stored directly on your computer, smartphone, or external drives. Full-disk encryption (FDE) tools like BitLocker (Windows) and FileVault (macOS) encrypt the entire contents of your hard drive. This protects all your files if your device is lost or stolen.
You can also use file-level or folder-level encryption to protect specific sensitive documents. Operating systems often provide built-in options, or you can use third-party software. This adds an extra layer of security for particularly important information stored locally on your machine.
These storage encryption methods typically rely on strong symmetric algorithms like AES. Access is usually tied to your user login password or a separate recovery key. This ensures that even with physical access to the storage media, the data remains inaccessible without proper authentication.
Secure Remote Connections with VPNs
A VPN (Virtual Private Network) creates a secure, encrypted “tunnel” for your internet traffic between your device and a remote VPN server. This hides your real IP address and encrypts your data, protecting your online activity, especially when using public Wi-Fi networks.
The encryption used by VPNs prevents Internet Service Providers (ISPs), network administrators, or potential eavesdroppers on public networks from seeing the websites you visit or the data you transmit. It enhances privacy and security significantly, particularly for remote workers or travelers.
VPNs employ various encryption protocols like OpenVPN, IKEv2/IPsec, or WireGuard. These protocols typically use a combination of symmetric (like AES for data) and asymmetric (for key exchange/authentication) cryptography to establish and maintain the secure, encrypted connection tunnel for user traffic.
Encryption Makes Your Digital Life Safer
Encryption is a fundamental security technology that protects information by making it unreadable without a key. It transforms readable plaintext into scrambled ciphertext using algorithms and keys. This process is vital for maintaining privacy and confidentiality in the digital age we live in.
It works behind the scenes in countless applications, from securing your online Browse (HTTPS) and private messages (E2EE) to protecting your Wi-Fi connection (WPA2/WPA3) and stored files (disk encryption). Understanding its role empowers you to appreciate and utilize digital security better.
The two main types, symmetric (shared key, like AES) and asymmetric (public/private keys, like RSA), offer different advantages and are often used together. Ultimately, encryption provides a powerful defense against data theft, surveillance, and unauthorized access, making the internet a safer place.
Frequently Asked Questions (FAQ) about Encryption
Even with a basic understanding, some common questions often arise about encryption. Let’s address a few frequently asked questions to further clarify how encryption works and its limitations, helping solidify your understanding of this critical security concept.
Is encryption unbreakable?
No encryption is theoretically “unbreakable,” but strong, modern encryption is computationally infeasible to break with current technology. Breaking well-implemented AES-256, for instance, would take the world’s fastest supercomputers billions of years using brute-force methods (trying every possible key).
However, encryption systems can be compromised in other ways. Weaknesses might exist in the algorithm itself (rare for standardized ones like AES), poor implementation, or, most commonly, through compromised keys. If an attacker steals the decryption key, the encryption becomes useless.
Therefore, while the mathematical scrambling provided by strong encryption is extremely robust, the overall security depends on proper implementation and rigorous key management practices. The emergence of quantum computing also poses a future threat, driving research into quantum-resistant algorithms (Post-Quantum Cryptography or PQC).
What’s the difference between encryption and hashing?
Encryption and hashing are both cryptographic techniques but serve different purposes. Encryption is a two-way process: data is encrypted (scrambled) and can be decrypted (unscrambled) back to its original form using a key. Its primary goal is confidentiality.
Hashing, conversely, is a one-way process. It takes an input (like a password or file) and produces a fixed-size string of characters (the hash value or digest). It’s impossible to reverse the hash to get the original input. Hashing is used mainly for integrity checking (verifying data hasn’t changed) and secure password storage.
When you log into a website, the system typically hashes the password you enter and compares it to a stored hash of your actual password. They don’t store or decrypt your actual password. This prevents attackers who steal the database from getting plaintext passwords, unlike reversible encryption.
Do I need special software to use encryption?
Often, you don’t need to install special software because encryption is built into many operating systems, browsers, and applications you already use. Your web browser handles HTTPS encryption automatically. Operating systems like Windows (BitLocker) and macOS (FileVault) offer built-in disk encryption.
Messaging apps like Signal implement end-to-end encryption seamlessly. However, for specific needs like encrypting individual files before emailing them or setting up more advanced configurations, you might choose to use dedicated encryption software or tools like VeraCrypt, GnuPG (GPG), or specialized enterprise solutions.
For everyday users, ensuring your software is up-to-date and enabling built-in security features (like disk encryption and secure Wi-Fi passwords) provides a significant level of protection without requiring extra technical steps or specialized software purchases in many common scenarios.
Can encrypted data still be hacked?
Yes, while the encrypted data itself is extremely difficult to decipher without the key, the systems holding it or the methods used to manage keys can still be compromised. Attackers often target weaknesses around the encryption rather than breaking the encryption directly.
Methods include stealing the decryption keys through malware, phishing attacks, or exploiting vulnerabilities in software. They might also compromise the device before data gets encrypted or after it’s decrypted. Weak passwords used for encryption keys can also be guessed or cracked.
Therefore, encryption is a crucial layer of security, but it’s not a silver bullet. It must be part of a comprehensive security strategy that includes strong passwords, up-to-date software, malware protection, secure key management, and user awareness to be truly effective against determined attackers.
