Have you ever wondered how businesses securely run their applications on shared public cloud infrastructure? A key part of the answer involves understanding the concept of a Virtual Private Cloud, often abbreviated as VPC. It’s a fundamental building block for modern cloud computing. This guide will break down exactly what a VPC is, how it works, its components, benefits, and common uses.
What is a Virtual Private Cloud (VPC)?
A Virtual Private Cloud (VPC) is essentially your own secure and isolated private network section that lives within a public cloud provider’s infrastructure (like AWS, Azure, or Google Cloud). It allows you to define and control a virtual network environment, including your own IP address ranges, subnets, route tables, and network gateways.
Think of it like having a private, fenced-off area within a large public park. The park itself is the public cloud provider’s shared infrastructure, but your fenced-off area (the VPC) is exclusively yours. You decide how it’s laid out (subnets), who can come in and out (security rules), and how it connects to paths outside your area (gateways).

Why Use a VPC?
- Enhanced Security: This is often the top reason. VPCs allow you to create multiple layers of security. You can use Security Groups (like firewalls for your virtual servers) and Network Access Control Lists (NACLs – firewalls for your subnets) to strictly control inbound and outbound traffic, significantly reducing the attack surface for your applications and protecting sensitive data.
- Granular Network Control: A VPC gives you command over your virtual network architecture. You define your own private IP address space, create subnets to segment resources logically (e.g., separating web servers from databases), configure custom route tables to dictate traffic flow, and manage network gateways precisely according to your needs.
- Resource Isolation: VPCs provide logical isolation, keeping your resources separate from those of other cloud customers. Furthermore, you can use subnets within your VPC to isolate different components of your applications from each other, preventing issues in one tier from easily affecting another and enhancing internal security.
- Hybrid Cloud Enablement: VPCs are crucial for building hybrid cloud solutions. They provide mechanisms (like VPN Gateways or dedicated connections like AWS Direct Connect/Azure ExpressRoute) to securely connect your cloud network environment back to your existing on-premises data centers, treating the cloud as a seamless extension of your private network.
- Meeting Compliance Requirements: Many industries and regulations (like PCI DSS, HIPAA) mandate specific network security and isolation standards. The control and security features inherent in VPCs help organizations implement the necessary configurations to meet these stringent compliance obligations.
How Does a Virtual Private Cloud Work?
A Virtual Private Cloud (VPC) works by using Software-Defined Networking (SDN) and network virtualization technologies on top of a public cloud provider’s physical infrastructure. Here’s a step-by-step breakdown of how it functions:
- Logical Isolation: Even though your resources might physically reside on hardware shared with other customers, the cloud provider uses sophisticated virtualization techniques to create a logically separate network just for you. Think of it as software creating impenetrable virtual walls around your network segment. Your network traffic is kept private and isolated from everyone else’s by default.
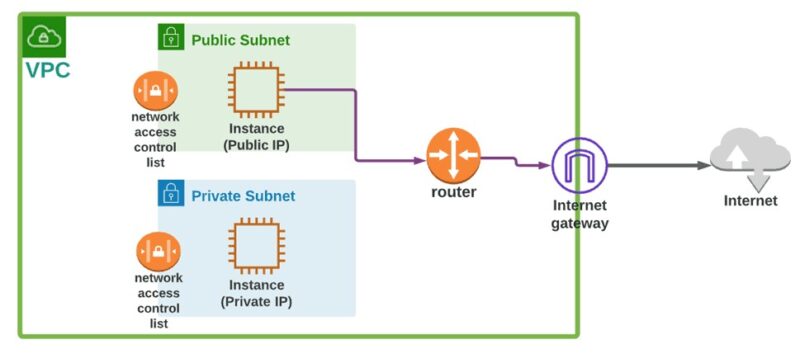
- Defining Your Network Space: You start by selecting a private IP address range (using CIDR notation, like 10.0.0.0/16) for your VPC. This becomes your exclusive address space within the cloud, ensuring no IP conflicts with other networks you might connect to later (like your office network).
- Creating Subnets: You then divide this large IP address range into smaller, manageable segments called subnets. Each subnet typically resides within a specific physical location (like an Availability Zone) for resilience. You place your cloud resources (virtual machines, databases, etc.) into these subnets.
- Controlling Traffic Flow:
- Route Tables: Each subnet is associated with a route table that acts like a virtual router. These tables contain rules that determine where network traffic originating from that subnet should go (e.g., to another subnet within the VPC, to the public internet via an Internet Gateway, or to your corporate network via a VPN Gateway).
- Security Rules: You apply virtual firewalls to control what traffic is allowed in or out. Security Groups act at the instance level (like a firewall on a specific virtual server), while Network Access Control Lists (NACLs) act at the subnet level (like a firewall for an entire network segment). You define rules based on protocols, ports, and IP addresses.
- Connecting Outward (Gateways): To connect your VPC to the internet or other networks, you use various types of gateways (like Internet Gateways, NAT Gateways, or VPN Gateways), which are managed by the cloud provider but configured according to your route table rules.
VPC vs. VPS
The key difference lies in their scope and purpose:
- A VPC is an entire private network environment that you create and control within a public cloud provider’s infrastructure. It’s about the networking that connects and isolates your resources.
- A VPS is a single virtual machine (server) instance that runs on shared physical hardware provided by a host. It’s about providing compute resources (CPU, RAM, OS) like a standalone server.
Here’s a comparison highlighting the main differences:
| Feature | Virtual Private Cloud (VPC) | Virtual Private Server (VPS) |
| What it IS | An isolated network environment or segment. | A single virtual machine / server instance. |
| Primary Role | Provides network infrastructure: isolation, subnets, routing, security rules. | Provides compute resources: Operating System, CPU, RAM, storage. |
| Scope | Contains potentially many resources (like multiple VMs/VPSs, databases, load balancers). | Is a single resource (a server) running an OS and applications. |
| Control | Control over the network configuration (IP ranges, subnets, routes, firewalls like SGs/NACLs). | Control (root/admin access) over the operating system and software on that specific server instance. |
| Analogy | Designing the secure layout and wiring for an entire private office floor within a larger building. | Renting one specific, private office room on that floor (or in another building). |
| Use Cases | Building multi-tier applications, secure corporate environments, hybrid clouds, complex network setups. | Hosting websites, running specific applications, development/test servers, simple server needs. |
| Offered By | Primarily major cloud providers (AWS, Azure, GCP) as part of IaaS. | Wide range of web hosting companies and cloud providers. |
Relationship:
You can think of it this way: a VPS (or a similar virtual machine like an AWS EC2 instance or Azure VM) is a type of compute resource that you might place inside the secure network boundaries provided by a VPC. To run most applications, you need both compute resources (like a VPS) and a network structure (like a VPC) to connect and protect them.
So, VPC handles the networking infrastructure, while VPS provides the server instance. They are different layers of the cloud stack.
VPC vs. VPN (Virtual Private Network)
Here’s the core difference:
- A VPC is the private network environment itself, hosted within a public cloud. It’s like building your own isolated network space in the cloud.
- A VPN is a technology that creates a secure, encrypted connection (tunnel) over a public network (like the internet). It’s about establishing a secure pathway for data transmission.
Here’s a more detailed comparison:
| Feature | Virtual Private Cloud (VPC) | Virtual Private Network (VPN) |
| Primary Role | Provides an isolated network environment or space within a public cloud. | Creates a secure connection or tunnel over an untrusted network. |
| Function | Hosts cloud resources (VMs, databases), defines subnets, manages routing, applies security rules (SGs/NACLs). | Encrypts data traffic between two points (e.g., user & network, or network & network) for secure transit. |
| What it IS | A place or infrastructure segment. | A method or technology for secure communication. |
| Scope | Encompasses a defined network segment with potentially many resources. | Typically point-to-point or client-to-network connectivity. |
| Analogy | Your secure, private office suite within a large shared office building. | The secure, encrypted courier service you use to send documents to your office suite. |
How they work together:
VPCs and VPNs are often used together. You might use a:
- Site-to-Site VPN: To create a secure, persistent connection between your company’s on-premises network (your physical office) and your VPC in the cloud, enabling a hybrid cloud setup.
- Remote Access VPN (Client VPN): To allow employees working remotely to securely connect their laptops to the resources running inside your VPC.
In summary: You build your secure house (VPC) in the cloud, and you use a secure tunnel (VPN) to get to it or connect it to another house. They solve different problems but are complementary technologies.
VPC vs. Physical Private Cloud
The fundamental difference is:
- A VPC is a logically isolated section built on shared infrastructure within a public cloud provider’s data center.
- A Physical Private Cloud utilizes dedicated hardware infrastructure reserved exclusively for a single organization.
Here’s a breakdown of the key distinctions:
| Feature | Virtual Private Cloud (VPC) | Physical Private Cloud |
| Infrastructure | Uses shared physical hardware owned and managed by a public cloud provider (e.g., AWS, Azure, GCP). | Uses dedicated physical hardware (servers, storage, networking) solely for one organization. |
| Isolation Method | Logical/Virtual isolation via Software-Defined Networking (SDN) and virtualization technologies. | Physical isolation (hardware is not shared with any other organization). |
| Location | Within the public cloud provider’s global data centers. | Can be on the organization’s premises (on-prem) or hosted in a third-party data center (hosted private cloud). |
| Scalability | High elasticity; resources typically provisioned/scaled rapidly on demand using provider tools. | Scalability depends on available dedicated hardware; often requires planning and procurement/provisioning cycles. Less elastic. |
| Cost Model | Primarily Operational Expenditure (OpEx); pay-as-you-go for resources consumed. | Often significant Capital Expenditure (CapEx) if built on-prem, plus ongoing OpEx. Hosted options involve recurring fees (OpEx). |
| Management | Shared responsibility model; provider manages physical infrastructure, organization manages virtual network, OS, applications. | Organization (or hosting provider) typically manages the entire stack, including hardware (if on-prem). |
| Hardware Control | No direct control over the underlying physical hardware. | Full control over hardware choices and configuration (especially if on-prem). |
| Multi-tenancy | Inherently multi-tenant at the physical hardware layer (but logically isolated). | Single-tenant; no sharing of hardware resources. |
In simple terms:
- Choose a VPC if you want the control and isolation of a private network combined with the scalability, elasticity, and pay-as-you-go benefits of the public cloud, without managing physical hardware.
- Choose a Physical Private Cloud if your organization requires dedicated hardware (perhaps for extreme security, compliance, or performance reasons), has the resources/desire to manage physical infrastructure (or pay a host), and elasticity needs are more predictable.
Both provide enhanced security and control compared to default public cloud offerings, but they achieve it through different means with different trade-offs in cost, management, and flexibility.
Common Virtual Private Cloud Use Cases
The benefits we’ve discussed translate directly into practical applications. VPCs are versatile and form the networking foundation for a wide array of cloud deployments. Here are some common scenarios where VPCs are essential:
- Hosting Multi-Tier Web Applications: A typical setup involves placing internet-facing web servers in a public subnet behind a load balancer. Application servers reside in a private subnet, and databases are further isolated in another private subnet, maximizing security.
- Running Databases and Backend Services Securely: Placing databases, caching servers, message queues, or internal APIs in private subnets ensures they are shielded from direct internet access, only reachable via controlled pathways from your application tiers.
- Extending Corporate IT Infrastructure is a major driver for VPC adoption in enterprises. By establishing secure VPN or Direct Connect links, companies can treat their VPC as a seamless extension of their existing data center network for hybrid cloud operations or disaster recovery.
- Organizations often use multiple VPCs for Creating Isolated Development, Testing, and Production Environments. This ensures that activities in non-production environments cannot accidentally impact live production systems, providing crucial separation and safety during the development lifecycle.
- Securely Processing Sensitive Data, such as financial transactions, personal identification information (PII), or health records, relies heavily on VPCs. The isolation and security controls help organizations meet strict data protection and compliance standards for handling such information.
- Connecting Multiple Business Units or Applications Privately is another key use case. Technologies like VPC Peering allow you to connect two VPCs directly using private IP addresses, enabling secure inter-VPC communication without traversing the public internet.
Frequently Asked Questions (FAQ)
Q1: Is a Virtual Private Cloud (VPC) free?
The VPC container itself is often free. However, certain components you deploy within or for your VPC typically incur costs. These can include NAT Gateways (charged per hour and per GB processed), VPN Gateway connections (charged per hour), and data transfer charges.
Q2: Is VPC considered Infrastructure as a Service (IaaS) or Platform as a Service (PaaS)?
VPC is fundamentally an Infrastructure as a Service (IaaS) offering. It provides you with control over core networking infrastructure components like virtual networks, subnets, and routing, upon which you build other services. PaaS typically abstracts more of the underlying infrastructure away.
Q3: Can multiple VPCs connect to each other?
Yes, multiple VPCs can be connected. Common methods include VPC Peering (connecting two VPCs directly within the same or different regions, allowing private communication) or using Transit Gateway (in AWS) or similar hub-and-spoke architectures to connect many VPCs and on-premises networks centrally.
Q4: What is the difference between a Security Group and a Network ACL (NACL)?
Security Groups act at the instance level, are stateful (return traffic automatically allowed), and only support ‘allow’ rules. NACLs act at the subnet level, are stateless (inbound and outbound rules must be explicit), and support both ‘allow’ and ‘deny’ rules processed in order.
