Ever wondered what a ‘port’ is, especially when dealing with computers or networks? Simply put, a network port is a virtual endpoint for communications, while a physical port is a hardware connection. This guide clearly explains both types, why they are crucial, and how they work using simple examples, helping you understand this fundamental concept of technology.
What is Port?
A network port is a logical, numbered endpoint created by a computer’s operating system. It doesn’t physically exist like a USB slot. Instead, it’s a virtual doorway used to manage network conversations. Each port is identified by a unique port number within that computer.
These virtual ports allow network traffic arriving at a single IP address (Internet Protocol address) to be correctly routed. They ensure data packets reach the intended application or service running on the device. Without ports, managing simultaneous network tasks would be impossible.
The IP Address + Port Number Analogy (Apartment Building Example)
Think of your computer’s IP address as the unique street address of a large apartment building. Many different families (applications) live in this building. How does mail (network data) get to the right family? It needs an apartment number – that’s the port number.
So, the combination of an IP address and a port number (like 192.168.1.100:80) creates a unique destination, often called a socket address. This tells network traffic exactly where to go: which building (IP address) and which specific apartment (port number) within that building.
Physical Ports vs. Network Ports: Key Differences Clarified
It’s vital to distinguish network ports (logical endpoints like Port 80) from physical ports (hardware connections). Physical ports are the tangible sockets you see on your computer or router, like USB ports, Ethernet ports (RJ45), or HDMI ports. You plug cables into these.
Network ports, however, are purely virtual constructs managed by software. They handle the flow of data for applications. While an Ethernet physical port connects your computer to the network, network ports manage the different conversations happening over that connection.
Why Are Network Ports Necessary?
Managing Multiple Conversations Simultaneously
The primary reason network ports exist is to allow a single device to handle many network conversations at the same time. Your computer uses one main network connection (identified by its IP address), but you often use multiple internet-based applications concurrently.
Imagine Browse several websites while your email client checks for new messages and a music app streams songs. Each of these activities requires a separate communication channel. Ports provide these distinct channels, preventing data streams from getting mixed up. This process is part of multiplexing and demultiplexing network traffic.
Directing Traffic to the Right Application
When data arrives at your computer’s IP address, the operating system needs to know which application should receive it. Is it data for your web browser, your game, or your file download manager? The port number included in the data packet header provides this crucial information.
Each network service or application “listens” on a specific port number or a range of ports. The operating system acts like a traffic director, reading the destination port number on incoming packets and forwarding them to the correct application. This ensures smooth and organized network communication.
Key Types of Network Ports: TCP vs. UDP
Network ports almost always work with one of two main transport layer protocols: TCP or UDP. These protocols define how data is sent and received using those port numbers. Understanding their differences is key to grasping how network communication functions.
Understanding Protocols: TCP and UDP Explained Simply
TCP stands for Transmission Control Protocol. It’s a reliable, connection-oriented protocol. Think of it like a phone call: a connection is established before data transfer begins, data is acknowledged upon receipt, and lost data is resent. This ensures all data arrives complete and in order.
UDP stands for User Datagram Protocol. It’s a simpler, faster, connectionless protocol. Think of UDP like sending a postcard: you send the data without establishing a prior connection, and there’s no guarantee it will arrive or in what order. It prioritizes speed over absolute reliability.
TCP Ports: For Reliable, Ordered Connections
TCP establishes a stable connection before any data is exchanged, using a process called the “three-way handshake.” This ensures both sender and receiver are ready. During transmission, TCP breaks data into ordered segments, tracks them, acknowledges receipt, and retransmits any lost segments.
Because of its reliability features, TCP is used for applications where data integrity and order are critical. Examples include web Browse (HTTP/HTTPS), email (SMTP, POP3/IMAP), and file transfers (FTP, SFTP). The overhead for ensuring reliability makes TCP slightly slower than UDP.
UDP Ports: For Fast, Lightweight Communication
UDP operates with minimal overhead. It simply sends data packets (datagrams) without setting up a connection or checking for delivery confirmation. This makes it much faster than TCP but less reliable. Packets might get lost, duplicated, or arrive out of order.
This speed makes UDP ideal for applications where timeliness is more important than perfect accuracy, or where occasional data loss is acceptable. Common uses include video and audio streaming, online gaming, DNS (Domain Name System) lookups, and Voice over IP (VoIP) calls.
Quick Comparison: When is TCP or UDP Used?
| Feature | TCP (Transmission Control Protocol) | UDP (User Datagram Protocol) |
|---|---|---|
| Connection | Connection-oriented (handshake required) | Connectionless (no handshake) |
| Reliability | High (acknowledgments, retransmission) | Low (best-effort delivery) |
| Ordering | Guarantees ordered packet delivery | No guarantee of order |
| Speed | Slower (due to overhead) | Faster (low overhead) |
| Use Cases | Web (HTTP/S), Email, File Transfer (FTP) | Streaming, Gaming, DNS, VoIP |
| Typical Example | Downloading a file completely and accurately | Live video stream where minor glitches are okay |
Decoding Port Number Ranges
Network ports are numbered from 0 to 65535. This entire range is divided into three categories, primarily managed by the IANA (Internet Assigned Numbers Authority), an organization responsible for coordinating global IP addressing and other internet numerical resources.
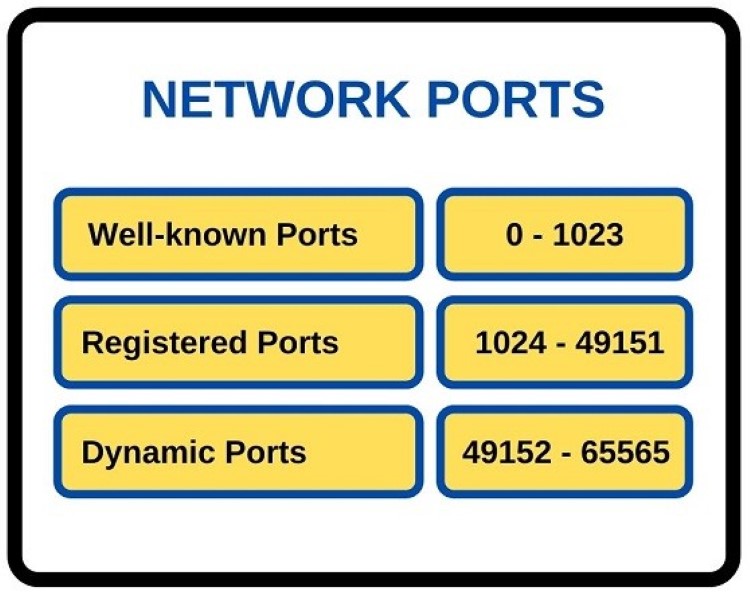
Well-Known Ports (0-1023): Standard Services
Ports in this range are reserved for standard, universally recognized internet services and protocols. Assigning a service to a port in this range generally requires administrative (root or administrator) privileges on the host operating system. This prevents unauthorized applications from using critical ports.
Examples include Port 80 for HTTP, Port 443 for HTTPS, Port 21 for FTP, Port 22 for SSH, and Port 53 for DNS. Using these standardized ports allows clients worldwide to easily connect to common services without needing custom configurations.
Registered Ports (1024-49151): Specific Applications
These ports are assigned by IANA upon request for specific applications or services. While not as strictly controlled as well-known ports, registering a port helps prevent conflicts between different software vendors. Many popular applications use registered ports.
Examples include Port 3389 for Microsoft Remote Desktop Protocol (RDP), Port 1433 for Microsoft SQL Server, Port 5432 for PostgreSQL, and Port 3306 for MySQL database servers. Users often don’t need administrative rights to use these ports.
Dynamic/Private Ports (49152-65535): Temporary Connections
Also known as ephemeral ports, these are not assigned to any specific service. They are typically used for temporary, outbound connections initiated by client applications. When your web browser connects to a website (on port 80 or 443), your computer assigns a random dynamic port for its end of the conversation.
This allows multiple connections to the same destination service (e.g., multiple browser tabs open to the same web server) without conflict, as each connection uses a different dynamic port on the client side. These ports are reused once the connection closes.
Who Assigns Port Numbers? The Role of IANA
The Internet Assigned Numbers Authority (IANA), a department of ICANN (Internet Corporation for Assigned Names and Numbers), coordinates the assignment of well-known and registered ports. This central coordination ensures global interoperability and prevents conflicts where multiple applications might try to use the same standard port number.
Common Network Ports and Their Everyday Uses
Understanding common ports helps demystify network traffic. Here are some frequently encountered ports and the services they typically handle:
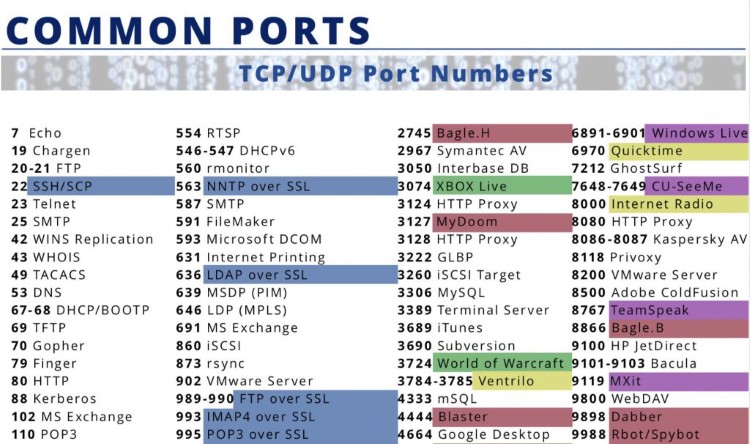
Port 80 (HTTP): The Foundation of the World Wide Web
HTTP (Hypertext Transfer Protocol) is the fundamental protocol used for transmitting web pages. When you type a http:// web address into your browser, it typically connects to the web server on TCP port 80 to request the page content (HTML, images, etc.).
Port 443 (HTTPS): Securing Your Web Browse
HTTPS (Hypertext Transfer Protocol Secure) is the encrypted version of HTTP. It uses TLS/SSL encryption to protect data exchanged between your browser and the web server. Most websites today use HTTPS, connecting via TCP port 443 to ensure privacy and security, especially for logins and transactions.
Port 21 (FTP) & 22 (SSH): File Transfer & Secure Logins
FTP (File Transfer Protocol, typically TCP port 21) is an older protocol for transferring files but sends credentials in plaintext (insecure). SFTP (SSH File Transfer Protocol), which runs over SSH (Secure Shell, typically TCP port 22), is the secure method for file transfers and remote server management via command line.
Port 25/587 (SMTP) & 110/995 (POP3) / 143/993 (IMAP): Sending and Receiving Email
SMTP (Simple Mail Transfer Protocol) is used for sending emails, commonly using TCP port 25 or 587 (for secure submission). POP3 (Post Office Protocol 3, TCP port 110 or 995 for secure) downloads emails to your device, often removing them from the server. IMAP (Internet Message Access Protocol, TCP port 143 or 993 for secure) synchronizes emails across multiple devices, leaving them on the server.
Port 53 (DNS): Translating Domain Names to IP Addresses
DNS (Domain Name System) acts like the internet’s phonebook, translating human-readable domain names (like www.google.com) into numerical IP addresses that computers use. DNS queries typically use UDP port 53 for speed, but can also use TCP port 53 for larger transfers.
Other Important Ports You Might Encounter
- RDP (Remote Desktop Protocol): TCP Port 3389, used for graphical remote access to Windows computers.
- DHCP (Dynamic Host Configuration Protocol): UDP Ports 67 & 68, used to automatically assign IP addresses to devices on a network.
- LDAP (Lightweight Directory Access Protocol): TCP/UDP Port 389, used for accessing directory services.
Ports, Firewalls, and Your Network Security
Network ports are closely tied to network security, particularly concerning firewalls. A firewall is a security system that monitors and controls incoming and outgoing network traffic based on predefined security rules. Ports play a crucial role in how firewalls operate.
What Does It Mean to ‘Open’ or ‘Close’ a Port?
An ‘open’ port means the computer is actively listening for incoming connections or data on that specific port number. A ‘closed’ port means the computer will reject connections attempted on that port, often sending back a message indicating it’s unreachable.
Configuring a firewall often involves specifying which ports should be open (allowed) and which should be closed (blocked) for incoming traffic. For example, a web server needs Port 80 and 443 open, but other ports might be closed for security.
Understanding Port Status: Open, Closed, Filtered
When checking port status (often done with port scanning tools), you might encounter three states:
- Open: The port is accepting connections.
- Closed: The port is reachable but no application is listening. It actively rejects the connection.
- Filtered: A firewall or filter is preventing access. The scanning tool cannot determine if the port is open or closed, often receiving no response.
Are Open Ports a Security Risk? (Context is Key)
An open port itself isn’t inherently a security risk; it’s necessary for network services to function. The risk comes from insecure or vulnerable applications listening on those open ports. If a service has known vulnerabilities, an attacker could potentially exploit the open port to gain unauthorized access.
Therefore, best practice involves minimizing the number of open ports to only those absolutely necessary (reducing the ‘attack surface’) and ensuring that the software listening on those ports is secure, updated, and properly configured. Unnecessary ports should be closed by a firewall.
Port Forwarding Explained: When and Why You Might Need It
Port forwarding (or port mapping) is a technique used on routers employing NAT (Network Address Translation). It allows external devices to connect to a specific device or service on a private local network by directing traffic arriving at the router’s public IP address on a specific port to an internal IP address and port.
Common uses include hosting a game server, accessing a home security camera system remotely, or running a personal web server. While useful, port forwarding must be done carefully, as it exposes internal services to the internet, potentially increasing security risks if not properly secured.
A Quick Look at Physical Computer Ports
While network ports are logical, physical ports are the tangible connectors on your devices. They serve different purposes but are equally vital for connecting hardware components and peripherals. Here are some common examples:
USB Ports (Type-A, Type-C): Connecting Almost Everything
USB (Universal Serial Bus) ports are ubiquitous for connecting peripherals like keyboards, mice, printers, external hard drives, and flash drives. USB Type-A is the classic rectangular connector. USB Type-C is the newer, smaller, reversible oval connector offering higher speeds and power delivery capabilities.
Ethernet Ports (RJ45): Your Wired Network Connection
The Ethernet port, using an RJ45 connector (which looks like a larger phone jack), provides a wired connection to a local network (LAN) or the internet via a router or modem. It generally offers a more stable and faster connection than Wi-Fi.
Display Ports (HDMI, DisplayPort, VGA): Connecting Monitors
These ports connect your computer to monitors or projectors. HDMI (High-Definition Multimedia Interface) is common for TVs and monitors, carrying both video and audio. DisplayPort is another digital standard popular for computer monitors, often supporting higher resolutions and refresh rates. VGA (Video Graphics Array) is an older analog standard, largely phased out.
Conclusion: Ports Are Essential Connectors in Technology
Ports, both virtual network ports and physical hardware ports, are fundamental building blocks of modern computing and networking. Network ports (like 80, 443, 22) act as numbered doorways, allowing multiple applications to communicate over a single network connection using protocols like TCP and UDP.
Physical ports (like USB, Ethernet, HDMI) provide the tangible interfaces to connect devices and peripherals. Understanding the difference and purpose of these port types helps demystify how computers interact with networks and each other, highlighting their critical role in our connected world.
Frequently Asked Questions (FAQ) About Ports
What’s the main difference between an IP address and a port number?
An IP address identifies a specific device (like a computer or server) on a network. A port number identifies a specific application or service running on that device. You need both to establish a connection correctly.
How many network ports can a computer technically have?
A computer can theoretically have 65,536 TCP ports and another 65,536 UDP ports. This is because port numbers range from 0 to 65535 for each protocol (TCP and UDP operate independently regarding port numbers).
Is it generally safe to have open network ports?
Having necessary ports open for required services (like Port 443 for a secure web server) is normal. However, unnecessarily open ports increase the potential attack surface. Safety depends on securing the applications listening on those ports and using firewalls to block unneeded access.
How can I find out which ports are open on my computer?
You can use built-in operating system tools like netstat (in Command Prompt/Terminal) or third-party port scanning software (like Nmap, use responsibly). These tools can show which ports your computer is listening on. Checking your router/firewall configuration also reveals forwarding rules.
Can a single port number be used by both TCP and UDP?
Yes, TCP and UDP are separate protocols. A service using TCP port 53 (like for large DNS transfers) is distinct from a service using UDP port 53 (standard DNS lookups). They don’t conflict as the protocol type is part of the unique endpoint identification.
Running applications effectively means understanding network ports and having solid hosting infrastructure. For quality, high-speed solutions, check out Vietnam VPS. They provide stable, reputable hosting with strong configurations featuring new generation dedicated hardware like AMD EPYC Gen 3 processors and NVMe U.2 SSDs, optimized capacity, high bandwidth, and advanced virtualization technology for high-end performance.
