Category Archives: Blog
What is Troubleshooting? Simple Steps to Solve Problems Effectively
Stuck with a problem you can’t solve, technical or otherwise? We’ve all been there! “Troubleshooting” [...]
What is Log Management? A Clear Guide for Beginners
Ever heard the term “Log Management” thrown around in IT, DevOps, or security discussions and [...]
What is Edge Computing? Explained Clearly (Benefits & Examples)
Edge computing is a way of processing data near where it is created, instead of [...]
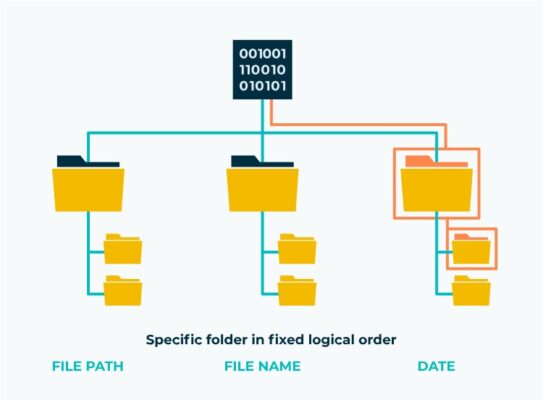
What Is File Storage? A Simple Explanation for Beginners
Ever saved a photo on your phone, written a document on your computer, or downloaded [...]
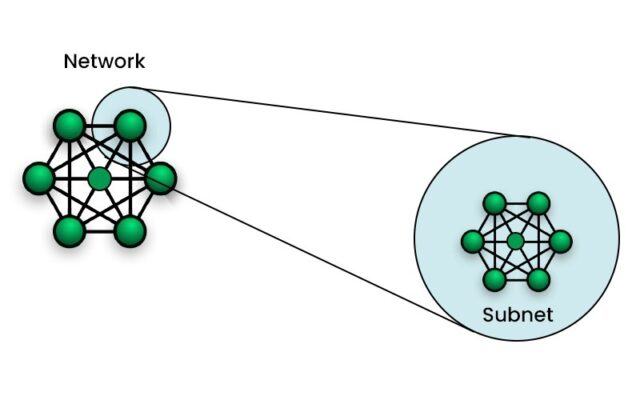
What is a Subnet? Understanding Network Segmentation
Managing large computer networks efficiently requires organization. Imagine trying to manage hundreds or thousands of [...]
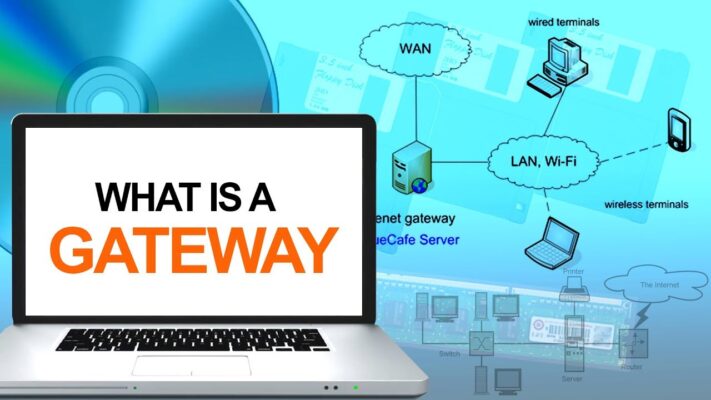
What is a Gateway in Networking? A Simple Explanation
Ever wondered how your home computer magically connects to the vast internet, or how different [...]
What Is Object Storage? A Clear Explanation
Object storage is a method for storing computer data that manages data as distinct units [...]
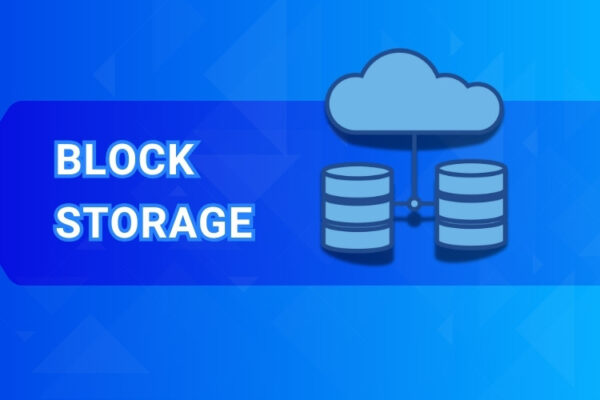
What is Block Storage? A Simple Explanation & Key Use Cases
Ever come across the term “block storage” when looking at cloud services, server specs, or [...]
What is a Domain Name? A Simple Explanation for Beginners
Ever wondered what people mean when they talk about a ‘website address’ or ‘domain name’? [...]
What is a DNS Server? The Internet’s Phonebook Explained
Ever wondered how typing www.google.com instantly takes you to Google? The magic behind that is [...]