A public key is a publicly shareable cryptographic code used to encrypt messages and verify digital signatures. It works together with a secret private key to secure digital communications and authenticate identities online. Understanding public keys is vital in our increasingly digital world.
Ever wondered how websites keep your information secure (that little padlock icon!), how cryptocurrencies work, or how secure login systems know it’s really you? Often, the answer involves something called a ‘public key’. It sounds technical, but the basic idea is quite straightforward and incredibly important.
Don’t worry if terms like ‘encryption’ or ‘cryptography’ seem daunting. This article will break down exactly what a public key is. We’ll explore how it works with its partner (the private key). You’ll also see where you encounter this technology every day – all explained in simple terms.
Public Key Definition
At its heart, a public key is a large numerical value. It’s part of a system called Asymmetric Cryptography, also known as Public Key Cryptography (PKC). This system uses two related keys: one public, one private. Think of them as a matched set.
The public key can be freely distributed without compromising security. You can share it with anyone. Its purpose is to allow others to send you encrypted data or verify your digital signature. It acts like a secure entry point for specific actions.

Think of it Like a Mailbox Address (A Simple Analogy)
Imagine you have a special mailbox with two keys. One key is for the mail slot (the public key). You can make copies of this slot key and give it to everyone. Anyone with this key can drop letters (encrypted data) into your mailbox.
The second key is the master key to open the mailbox itself (the private key). Only you have this key. While anyone can put mail in using the public slot key, only you can open the mailbox and read the letters using your unique private key.
This analogy highlights the core function: the public key provides a way for others to securely send things to you. The private key ensures only you can access what’s sent. It separates the ability to encrypt from the ability to decrypt.
What Makes a Public Key “Public”?
The term “public” means it’s designed for sharing. You can post it on your website, print it on a business card, or list it in public directories (like PGP key servers). Sharing your public key doesn’t put your sensitive information at risk.
This is because the public key, by itself, cannot be used to figure out the corresponding private key. The mathematical relationship is designed to be a one-way street. It’s easy to calculate the public key from the private key, but practically impossible to reverse the process.
This one-way function is the foundation of public key cryptography’s security. It allows for open distribution of one key while maintaining the secrecy of the other. This enables secure interactions between parties who may have never met or established a prior secure channel.
Public Key vs Private Key: Understanding the Essential Pair
Public and private keys don’t exist in isolation; they are generated together as a unique Key Pair. They are mathematically linked. What one key encrypts, only the other key in the pair can decrypt. What one key signs, only the other can verify.
This two-key system is the defining feature of asymmetric cryptography. It solves a major challenge faced by older systems: how to share a secret key securely in the first place. With asymmetric crypto, you never need to share your private key.
Meet the Secret Keeper: What is a Private Key?
A Private Key is the secret half of the key pair. It’s a large numerical value that you must keep absolutely confidential. If someone gains access to your private key, they can decrypt messages meant only for you and impersonate you by forging your digital signature.
Protecting your private key is paramount. It’s often stored in a password-protected file, on a hardware security device, or within secure system software. Loss or compromise of the private key fundamentally breaks the security provided by the key pair.
Think back to the mailbox analogy: the private key is the physical key that opens the box. You wouldn’t make copies of that key and hand them out – you keep it safe and secure.
How Public and Private Keys Work Together
The magic lies in their mathematical relationship. Key pairs are typically generated using complex algorithms like RSA (Rivest–Shamir–Adleman) or ECC (Elliptic Curve Cryptography). These algorithms create two keys with specific properties:
- Data encrypted with the public key can only be decrypted using the corresponding private key.
- Data signed with the private key can only be verified using the corresponding public key.
This complementary action allows for both confidentiality (keeping messages secret) and authenticity (proving who sent a message or created data). The specific function depends on which key is used for the initial action (encryption or signing).
A Quick Look at Asymmetric Cryptography
Asymmetric cryptography uses two keys (public and private). This differs from Symmetric Cryptography, which uses only a single, shared secret key for both encryption and decryption. Think of symmetric crypto like a simple door lock where the same key locks and unlocks it.
Symmetric encryption is generally faster. However, it faces the “key exchange problem”: how do two parties securely share the single secret key without someone intercepting it? Asymmetric cryptography elegantly solves this. You can safely share the public key over insecure channels.
Often, systems use a hybrid approach. Asymmetric cryptography (using the public/private key pair) is used initially to securely exchange a temporary, single-use symmetric key. The rest of the communication then uses the faster symmetric encryption with that securely exchanged key. This is common in protocols like TLS.
How Do Public Keys Actually Work? (Key Functions)
Public keys enable two primary security functions: encrypting data so only the intended recipient can read it, and verifying digital signatures to ensure authenticity and integrity. Let’s look at how the public key facilitates these scenarios.
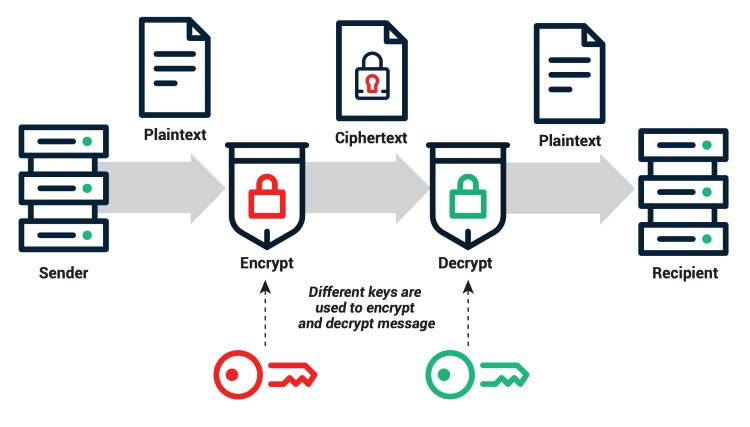
Function 1: Receiving Encrypted Information Securely
Imagine Alice wants to send a confidential message to Bob. She doesn’t want anyone else, like eavesdropper Eve, to read it. Here’s how public key encryption works:
- Bob shares his Public Key: Bob makes his public key available to Alice (e.g., emails it, posts it online).
- Alice Encrypts: Alice uses Bob’s public key and an encryption algorithm to scramble her message. The resulting encrypted text looks like random gibberish.
- Alice Sends: Alice transmits the encrypted message to Bob over any channel (even an insecure one).
- Eve Intercepts (Optional): If Eve intercepts the message, she cannot read it. She only has the encrypted data and Bob’s public key, which cannot decrypt the message.
- Bob Decrypts: Bob receives the message and uses his private key (which only he possesses) to decrypt it, restoring the original confidential text.
In this process, Bob’s public key acts like an open padlock that Alice uses to lock the message box. Only Bob has the unique key (his private key) to unlock it.
Function 2: Verifying Digital Signatures
Now, imagine Bob wants to send Alice a document and prove it genuinely came from him and hasn’t been tampered with. This uses digital signatures, leveraging the key pair in reverse:
- Bob Creates a Hash: Bob takes his document and runs it through a Hash Function. This creates a small, fixed-size fingerprint of the document called a hash (e.g., SHA-256). Even a tiny change to the document results in a completely different hash.
- Bob Signs (Encrypts Hash): Bob uses his private key to encrypt this hash value. This encrypted hash is the Digital Signature.
- Bob Sends: Bob sends the original document along with the digital signature to Alice.
- Alice Verifies: Alice receives the document and the signature. She performs two steps:
- She uses Bob’s public key to decrypt the digital signature. This reveals the original hash value Bob created.
- She independently calculates the hash of the document she received using the same hash function Bob used.
- Alice Compares: Alice compares the hash she calculated with the hash she decrypted from the signature. If they match, she knows two things:
- Authenticity: Only Bob’s private key could have created a signature verifiable by his public key. So, the document came from Bob.
- Integrity: The document hasn’t been altered since Bob signed it. If it had been changed, the hashes wouldn’t match.
Here, Bob’s private key is used to create the signature (like a unique seal), and his public key is used by others to verify that seal is authentic.
Where You Encounter Public Keys in Daily Life (Common Uses)
Public key cryptography isn’t just theoretical; it’s the backbone of much of our modern digital security. You interact with it frequently, often without realizing it. Here are some key examples:
Securing Your Browse: HTTPS and SSL/TLS Certificates
When you visit a website using HTTPS (Hypertext Transfer Protocol Secure), you see a padlock icon in your browser’s address bar. This indicates a secure connection established using SSL/TLS (Secure Sockets Layer / Transport Layer Security) protocols.
Here’s how public keys are involved:
- Your browser connects to the website’s server.
- The server responds by sending its SSL/TLS Certificate. This certificate contains the server’s public key and information verifying the server’s identity, usually issued by a trusted Certificate Authority (CA).
- Your browser uses the CA’s public key (pre-installed in the browser) to verify the server’s certificate signature.
- Your browser then uses the server’s now-verified public key to securely negotiate a temporary symmetric key for encrypting the actual data exchanged during your session.
The public key in the server’s certificate is crucial for authenticating the server (proving it’s the legitimate site, not an imposter) and initiating the secure channel. Billions of connections rely on this every day. According to Google’s Transparency Report, over 95% of pages loaded in Chrome globally (as of early 2025) use HTTPS.
Logging In Securely: SSH Keys
SSH (Secure Shell) is a protocol used for secure remote login and command execution, typically between computers over a network. While SSH can use passwords, public key authentication is considered far more secure.
- Key Generation: The user generates an SSH key pair (public and private key) on their local machine.
- Public Key Deployment: The user copies their public key to the
.ssh/authorized_keysfile on the remote server they want to access. - Authentication: When the user tries to connect:
- The server recognizes the user and finds their public key in the
authorized_keysfile. - The server sends the user a challenge message encrypted with their public key (or uses the key in a challenge-response protocol).
- The user’s SSH client software automatically uses the private key (stored securely on the local machine) to decrypt the challenge or respond correctly.
- The server recognizes the user and finds their public key in the
- Access Granted: If the decryption/response is successful, the server verifies the user possesses the corresponding private key and grants access without needing a password.
This method prevents password theft and brute-force attacks, commonly used by system administrators and developers for secure server management.
Protecting Your Emails: PGP/GPG Encryption
PGP (Pretty Good Privacy) and its open-source alternative GPG (GNU Privacy Guard) use public key cryptography to encrypt emails and files.
- Users generate a PGP/GPG key pair.
- They share their public keys with contacts (often via email signatures or public key servers).
- To send an encrypted email to someone, you use their public key to encrypt the message content. Only they can decrypt it with their private key.
- To sign an email, you use your private key to create a digital signature. Recipients use your public key to verify the signature, confirming authenticity and integrity.
This provides end-to-end encryption and authentication for sensitive email communications, widely used by journalists, activists, and security-conscious individuals.
Powering Cryptocurrencies: Blockchain, Wallets, and Addresses
Public key cryptography is fundamental to how cryptocurrencies like Bitcoin and Ethereum operate.
- Wallet Generation: When you set up a cryptocurrency Wallet, it generates one or more key pairs.
- Public Key to Address: Your Cryptocurrency Address (the string of characters you share to receive funds) is typically derived from your public key through hashing and encoding. Think of the address as a user-friendly version of the public key concept.
- Receiving Funds: You share your public address. Others use it to send cryptocurrency to your wallet. The transaction is recorded on the Blockchain.
- Spending Funds: To send cryptocurrency from your wallet, you must create a transaction and sign it using your private key. This proves you own the funds associated with that address.
- Verification: Nodes on the blockchain network use your public key (derived from the address) to verify the digital signature on the transaction before confirming it. This prevents unauthorized spending.
The entire security model of decentralized cryptocurrencies relies on users securely managing their private keys while public keys (and derived addresses) facilitate transactions and verification on the public ledger.

Answering Your Questions About Public Keys (FAQ)
Let’s address some common questions about public keys to solidify understanding.
Is it Safe to Share My Public Key?
Yes, it is generally safe and intended to be shared. Sharing your public key allows others to send you encrypted messages or verify your digital signatures. It does not reveal your private key or compromise your security, thanks to the one-way mathematical relationship between the keys.
However, be mindful of context. Sharing your public key reveals that you use cryptography, which might be relevant in some situations. Also ensure people receive your correct public key to avoid man-in-the-middle attacks during key exchange. Use trusted channels or verification methods when possible.
How Do I Get or Generate a Public Key?
You typically don’t create public keys manually from scratch. Instead, you use software designed for specific purposes that generates a key pair (both public and private keys) together.
- SSH: Tools like
ssh-keygenon Linux/macOS or PuTTYgen on Windows generate SSH key pairs. - PGP/GPG: Software like Gpg4win (Windows), GPG Suite (macOS), or command-line
gpggenerate PGP key pairs. - Cryptocurrency Wallets: Wallet software (e.g., Exodus, MetaMask, hardware wallets like Ledger) automatically generates key pairs when you create a new wallet or account.
- Websites (SSL/TLS): Server administrators generate a key pair as part of creating a Certificate Signing Request (CSR) to obtain an SSL/TLS certificate.
The software securely stores the private key and provides the public key for you to share or deploy as needed.
How is This Different From Symmetric Key Cryptography?
The main difference lies in the number of keys used:
- Asymmetric (Public Key) Cryptography: Uses two keys – a public key for encryption/verification and a private key for decryption/signing. Solves key exchange issues but is slower.
- Symmetric Cryptography: Uses one shared secret key for both encryption and decryption. It’s faster but requires a secure method to share the key initially.
Modern systems like TLS often use both: asymmetric to securely establish a connection and exchange a temporary symmetric key, then symmetric for the bulk data transfer, getting the best of both worlds.
Wrapping Up: Why Public Keys Are Foundational to Digital Security
Public keys are a cornerstone of modern digital security and trust online. They are the publicly shareable half of a mathematically linked key pair used in asymmetric cryptography. While the private key remains secret for decryption and signing, the public key enables secure encryption and signature verification.
From securing your online Browse and logins (HTTPS, SSH) to protecting emails (PGP) and enabling cryptocurrencies, public key cryptography works behind the scenes constantly. Understanding the basic principles of how public and private keys interact helps demystify how digital security functions.
While the underlying mathematics is complex, the concept is powerful: a system allowing secure communication and authentication without needing to share a secret beforehand. This innovation continues to underpin trust and security across the internet.
Deploying secure services, like those using public keys for SSH or SSL/TLS, requires dependable infrastructure. Consider Vietnam VPS for high-speed, stable hosting built on new generation dedicated hardware including AMD EPYC Gen 3 CPUs and NVMe U.2 SSDs. Experience optimized capacity, high bandwidth, and advanced virtualization for quality, cost-effective performance across their offerings.
