In today’s complex digital landscape, proactively identifying security weaknesses is essential. That’s where vulnerability scanning comes in. So, what exactly is it? This guide provides a clear explanation of what vulnerability scanning involves, how the process works, the different types of scans, its key benefits, and how it fits into a larger security strategy.
Defining Vulnerability Scanning
At its core, vulnerability scanning is an automated security assessment technique. It employs specialized software tools, known as vulnerability scanners, to systematically probe defined targets within an IT environment. These targets can include servers, workstations, network devices, web applications, databases, and cloud infrastructure.
The main function is identification, not exploitation. Scanners check targets against vast databases of known vulnerabilities – weaknesses that have already been discovered and documented publicly, often cataloged with unique identifiers like CVE (Common Vulnerabilities and Exposures) numbers. They look for signatures or configurations matching these known flaws.
Think of it as an automated security check-up for your IT assets. It’s designed to be performed regularly and systematically, providing a snapshot of potential weaknesses based on current knowledge. This proactive approach contrasts sharply with reactive measures taken only after a security incident occurs.
Unlike manual security testing, vulnerability scanning leverages automation for speed and breadth. It can quickly assess large numbers of systems for thousands of known potential issues, making it a cornerstone of modern cybersecurity practices for organizations of all sizes.

Why Do Organizations Perform Vulnerability Scans?
Organizations implement vulnerability scanning programs for several critical reasons, all aimed at improving their overall security posture and reducing the risk associated with cyber threats. Understanding these drivers highlights the importance of this automated security assessment process.
The primary purpose of vulnerability scanning includes:
- Identify Weaknesses Early: The most fundamental goal is to find security vulnerabilities, misconfigurations, and missing patches before attackers discover and exploit them. This significantly reduces the organization’s attack surface – the number of potential entry points for intruders.
- Manage Cybersecurity Risk: Scan results provide vital data for risk assessment. By identifying potential weaknesses and their severity, organizations can understand their exposure and make informed decisions about where to focus security resources and mitigation efforts.
- Meet Compliance Requirements: Many industry regulations and security standards mandate regular vulnerability scanning. For example, the Payment Card Industry Data Security Standard (PCI DSS) explicitly requires quarterly internal and external vulnerability scans for organizations handling credit card data. HIPAA and GDPR also imply its necessity for protecting sensitive data.
- Prioritize Remediation Efforts: Scan reports typically prioritize findings based on severity (often using the CVSS scoring system). This helps IT and security teams efficiently allocate resources to fix the most critical issues first, optimizing the patch management and remediation workflow.
- Improve Security Posture Visibility: Regular scanning provides ongoing visibility into the security health of IT assets. It helps maintain an accurate inventory and track whether security controls are effective and configurations remain secure over time, preventing configuration drift.
How Vulnerability Scanning Works
Vulnerability scanning follows a methodical, automated process powered by specialized scanner tools. While the specifics vary between tools, the core workflow generally involves several key steps to identify potential weaknesses within the targeted IT environment.
Here’s a breakdown of how the typical vulnerability scanning process unfolds:
Configuration & Targeting
The process begins with configuring the vulnerability scanner. This involves defining the scope of the scan – specifying which IP addresses, network ranges, hostnames, web application URLs, or cloud environments should be assessed. Scan policies, intensity levels, and schedules are also set during this phase.
For certain scan types (authenticated scans), administrators provide the scanner with login credentials (like a Windows domain account or SSH key). This allows the scanner to log into target systems for deeper inspection, significantly improving accuracy and coverage compared to unauthenticated scans.
Probing & Information Gathering
Once configured, the scanner actively probes the defined targets over the network. It attempts to discover live hosts, open TCP and UDP ports, and the services running on those ports. It gathers information like operating system types, service banner details, and software versions.
This discovery or enumeration phase helps the scanner understand the landscape it needs to assess. For web application scans, this involves crawling the application to identify pages, forms, parameters, and technologies used (like specific frameworks or server types).
Vulnerability Database Comparison
This is the core analysis step. The scanner takes the information gathered about each target (OS version, service versions, open ports, configurations) and compares it against its extensive, built-in vulnerability database. This database contains signatures and checks for thousands of known vulnerabilities.
These database entries are constantly updated by the scanner vendor and are often linked to CVE identifiers. A CVE provides a unique reference number for a specific, publicly known cybersecurity vulnerability, allowing for standardized tracking and communication about flaws across different tools and platforms.
Analysis & Reporting
If the scanner finds characteristics on a target system that match a known vulnerability signature in its database, it flags a potential finding. For example, detecting a specific outdated version of web server software known to contain CVE-2023-XXXX would result in a vulnerability being reported.
After scanning all targets, the tool compiles a detailed vulnerability scan report. This report lists all identified potential vulnerabilities, the assets affected, evidence supporting the finding, and crucially, a severity rating, typically based on the CVSS (Common Vulnerability Scoring System).
The CVSS score (ranging from 0.0 to 10.0) helps prioritize remediation efforts by indicating the technical severity of each vulnerability based on factors like exploit complexity, potential impact, and required privileges. Reports often include links to CVE details and suggested remediation actions.
Understanding the Different Types of Vulnerability Scans
Vulnerability scanning is not a one-size-fits-all process. Different types of scans exist, each offering a unique perspective and focusing on specific aspects of the IT environment. Choosing the right types of scans is crucial for comprehensive security assessment.
Here are the main categories:
Internal vs. External Scans
This distinction relates to the network vantage point of the scan:
- External Vulnerability Scans: These are performed from outside the organization’s network perimeter, simulating the view of an attacker on the internet. They target internet-facing assets like web servers, email servers, VPN gateways, and firewalls, looking for weaknesses exposed externally.
- Internal Vulnerability Scans: These are conducted from inside the corporate network. They simulate the perspective of an insider threat or an attacker who has already breached the perimeter. Internal scans assess servers, workstations, databases, and other internal assets for vulnerabilities exploitable from within. PCI DSS, for instance, requires both types quarterly.
Authenticated vs. Unauthenticated Scans
This relates to whether the scanner uses login credentials:
- Unauthenticated (Non-credentialed) Scans: The scanner interacts with targets without logging in, mimicking an attacker with no prior access. It identifies vulnerabilities detectable through network probes and service banners but cannot see detailed configurations or patch levels requiring login. Results often contain more false positives.
- Authenticated (Credentialed) Scans: The scanner uses provided credentials (e.g., domain user, SSH key) to log into target systems. This allows for much deeper inspection of installed software versions, precise patch levels, local configurations, and running processes, leading to more accurate results and fewer false positives. It’s essential for comprehensive host-based assessment.
Network, Host, and Application Scans
This categorizes scans by the type of asset being targeted:
- Network Scans: Focus on network infrastructure devices (routers, firewalls, switches) and identifying open ports, running network services, and potential vulnerabilities in network protocols across ranges of IP addresses.
- Host-Based Scans: Concentrate on individual servers or workstations. Often authenticated, they delve deep into the operating system configuration, installed applications, user accounts, and specific patch levels to find OS and third-party software vulnerabilities.
- Web Application Scans: Specifically designed to find vulnerabilities common in web applications and APIs, such as Cross-Site Scripting (XSS), SQL Injection, insecure authentication mechanisms, and configuration errors. This often uses techniques associated with DAST (Dynamic Application Security Testing).
Other Specialized Scan Types
Depending on the environment, other specialized scans may be employed:
- Database Scans: Focus on database servers (like SQL Server, Oracle, MySQL) looking for weak passwords, insecure configurations, missing patches, or excessive user privileges specific to database environments.
- Cloud Configuration Scans: Assess the security settings of resources deployed in cloud platforms (AWS, Azure, GCP), checking for misconfigurations in storage buckets, security groups, IAM policies, etc.
- Container Scans: Analyze container images (e.g., Docker images) for known vulnerabilities in base images, application code, and dependencies before deployment, as well as scanning running containers.
Scan Outputs and Key Benefits
Performing vulnerability scans yields valuable information and provides significant advantages for an organization’s cybersecurity program. Understanding the typical outputs and resulting benefits helps justify the investment in regular scanning activities.
The Vulnerability Scan Report
The primary output is a detailed report summarizing the findings. Key components usually include:
- List of Affected Assets: Identifies the specific IP addresses, hostnames, or application URLs where vulnerabilities were detected.
- Detected Vulnerabilities: Describes each potential vulnerability found, often including its CVE identifier for standardized reference.
- Severity Rating: Assigns a score (typically CVSS) to each vulnerability, indicating its criticality (e.g., Critical, High, Medium, Low) to aid prioritization.
- Evidence/Details: Provides information supporting the finding, such as the port/service involved, software version detected, or specific configuration issue observed.
- Remediation Recommendations: Often includes suggestions for fixing the vulnerability, such as links to vendor patches, configuration guidance, or mitigating controls.
Major Advantages and Benefits
Regular vulnerability scanning delivers substantial benefits:
- Reduced Risk of Breaches: Proactively identifying and fixing weaknesses significantly lowers the chances of attackers successfully compromising systems and causing data breaches.
- Enhanced Compliance: Helps organizations meet and demonstrate compliance with regulatory requirements (PCI DSS, HIPAA, GDPR) and security frameworks (NIST, ISO 27001) that mandate vulnerability assessment.
- Improved Remediation Efficiency: Prioritized reports based on severity allow security teams to focus resources on fixing the most critical issues first, optimizing patch management and remediation efforts.
- Increased Security Visibility: Provides ongoing insight into the security posture of the IT environment, helping to track trends, verify security controls, and maintain an accurate asset inventory.
- Cost Savings: Preventing a single major breach through proactive scanning can save enormous costs related to incident response, recovery, regulatory fines, legal fees, and reputational damage. Automation also makes broad scanning cost-effective.
The Tools of the Trade: Vulnerability Scanners
The entire vulnerability scanning process is enabled by specialized software tools known as vulnerability scanners. These tools automate the complex tasks of probing targets, analyzing responses, comparing findings against vast databases, and generating reports.
Vulnerability scanners come in various forms:
- Commercial Solutions: Widely used options from vendors like Tenable (Nessus), Qualys (Cloud Platform), and Rapid7 (InsightVM/Nexpose) offer extensive features, large vulnerability databases, support, and compliance reporting capabilities. Many operate as SaaS (Software as a Service) platforms.
- Open-Source Tools: Options like OpenVAS (now Greenbone Vulnerability Management) provide powerful scanning capabilities free of charge, though they may require more manual setup and configuration and might lack the extensive support or reporting features of commercial tools.
- Specialized Scanners: Tools exist that focus specifically on certain areas, such as web application scanners (Acunetix, Burp Suite Pro Scanner) or cloud security posture management (CSPM) tools with scanning features.
The choice of scanner depends on factors like budget, the size and complexity of the environment, compliance requirements, required features (e.g., authenticated scanning, specific target types), and available technical expertise within the organization.
Important Limitations and Considerations
While vulnerability scanning is an indispensable security practice, it’s crucial to understand its limitations to set realistic expectations and complement it with other security measures. No single tool or process offers complete protection.
Key limitations include:
- Focus on Known Vulnerabilities: Scanners primarily detect vulnerabilities that are already publicly known and included in their database (CVEs). They are generally not effective at finding zero-day vulnerabilities (previously unknown flaws) or complex business logic flaws in custom applications.
- Potential for False Positives: Scanners can sometimes misinterpret system responses and report a vulnerability that doesn’t actually exist. Security teams must investigate and validate findings to avoid wasting resources on non-issues. This requires expertise and time.
- Potential for False Negatives: Conversely, a scanner might fail to detect a real vulnerability. This can happen if the vulnerability signature is missing or inaccurate, if the scan configuration is suboptimal (e.g., unauthenticated scan missing internal flaws), or if the vulnerability requires complex interaction to trigger.
- Typically Non-Intrusive: Most vulnerability scans are designed to identify weaknesses without actively exploiting them. This means a scan report indicates potential risk, but doesn’t definitively confirm if a vulnerability is exploitable in that specific environment’s context. Some tools offer limited validation features.
- Requires Context for Prioritization: While CVSS scores provide a technical severity rating, effective risk management requires considering business context – asset criticality, data sensitivity, potential impact, and existing compensating controls – to truly prioritize remediation efforts.
Understanding these limitations helps organizations use scan results effectively as part of a broader, layered security strategy, rather than relying on scanning as a silver bullet.
Vulnerability Scanning vs. Penetration Testing: What’s the Difference?
A common point of confusion is the difference between vulnerability scanning and penetration testing (pentesting). While both aim to improve security by finding weaknesses, they employ fundamentally different approaches and serve distinct, albeit complementary, purposes. Understanding this distinction is vital.
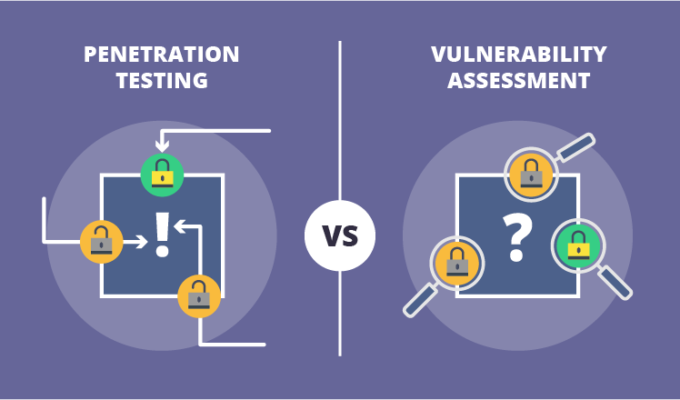
Here’s a breakdown of the key differences:
- Goal:
- Vulnerability Scanning: To broadly identify and inventory known potential vulnerabilities across many systems using automated tools. Answers: “What might be wrong?”
- Penetration Testing: To simulate a real-world attack by attempting to actively exploit identified vulnerabilities to determine if they are truly exploitable and assess the potential business impact. Answers: “Can someone break in, how, and what could they access?”
- Method:
- Vulnerability Scanning: Primarily automated, relying on scanners and vulnerability databases. Focuses on breadth.
- Penetration Testing: Primarily manual (though uses tools), involving creative thinking, problem-solving, and simulating attacker techniques. Focuses on depth and impact.
- Frequency:
- Vulnerability Scanning: Typically performed frequently (e.g., weekly, monthly, quarterly, or continuously) to keep up with new vulnerabilities and system changes.
- Penetration Testing: Usually conducted less frequently (e.g., annually or biannually) due to its intensive nature and cost.
- Output:
- Vulnerability Scanning: Generates a list of potential vulnerabilities, often prioritized by technical severity (CVSS).
- Penetration Testing: Produces a report detailing successfully exploited vulnerabilities, the attack paths used, the extent of compromise achieved, and actionable recommendations based on proven risk.
- Analogy:
- Vulnerability Scanning: Like getting a broad health check-up or inspecting all the doors and windows of a building for potential weaknesses (unlocked, broken).
- Penetration Testing: Like hiring someone to actually try breaking into the building using identified weaknesses to see if they can get past the locks and security systems.
Neither process replaces the other; they work best together. Scanning provides regular, broad coverage, while pentesting provides deep validation and real-world risk assessment.
Where Scanning Fits: The Vulnerability Management Lifecycle
Vulnerability scanning is not an isolated activity but rather a critical component of a larger, continuous process known as Vulnerability Management. This lifecycle approach provides a structured framework for systematically identifying, assessing, prioritizing, and remediating security weaknesses over time.
The typical phases of the vulnerability management lifecycle include:
- Discover: Identifying and creating an inventory of all IT assets within the organization’s environment (servers, devices, applications, cloud resources). You can’t protect what you don’t know you have.
- Assess: This is where vulnerability scanning plays its primary role. Scans are performed on discovered assets to identify potential vulnerabilities. Penetration testing may also occur in this phase for deeper assessment.
- Prioritize: Analyzing the results from the assessment phase. Findings are prioritized based on factors like CVSS severity, asset criticality, business impact, exploit availability, and threat intelligence to determine which vulnerabilities pose the greatest risk and require immediate attention.
- Remediate: Taking action to fix or mitigate the prioritized vulnerabilities. This typically involves applying vendor patches (patch management), changing configurations, implementing compensating controls, or retiring vulnerable systems.
- Verify: After remediation actions are taken, rescanning the affected assets is crucial to verify that the vulnerability has been successfully addressed and the fix is effective.
- Report & Improve: Continuously monitoring the process, tracking key metrics (e.g., time-to-patch), reporting on the organization’s risk posture, and refining the vulnerability management program based on lessons learned.
Vulnerability scanning provides the essential data feed for the assessment, prioritization, and verification stages of this critical ongoing security process.
In conclusion, vulnerability scanning is an essential, foundational practice for any organization serious about cybersecurity. This automated process provides the necessary visibility into known security weaknesses across your IT environment, enabling proactive risk management and remediation before attackers can strike.
While it has limitations and doesn’t replace other crucial security measures like penetration testing or robust incident response capabilities, regular and well-managed vulnerability scanning is indispensable. It helps meet compliance demands, optimizes patching efforts, and significantly strengthens your overall security posture against a constantly evolving threat landscape.
By understanding what vulnerability scanning is, how it works, its benefits, and its place within a comprehensive vulnerability management program, organizations can leverage this powerful tool effectively. Make consistent scanning a core part of your security routine to better protect your valuable assets and data.
