Understanding IPS technology is crucial in today’s cybersecurity landscape. It often works alongside other defenses like firewalls and Intrusion Detection Systems (IDS). This article provides a clear explanation of what an IPS is, its purpose, how it functions, different types, benefits, and key considerations.
What is an Intrusion Prevention System (IPS)?
An Intrusion Prevention System (IPS) is a network security technology. It can be a dedicated hardware appliance or a software application. Its core function is to continuously monitor network or system activities for any signs of malicious behaviour or policy violations.
Unlike its cousin, the Intrusion Detection System (IDS) which primarily detects and alerts, an IPS takes a crucial step further. It provides active threat prevention. This means it doesn’t just report potential problems; it automatically takes action to block or stop them in real-time.
The main goal of an IPS is fourfold: identify malicious activity, log detailed information about this activity, report it to administrators, and most importantly, attempt to block or stop it before it compromises systems or data. It acts proactively to maintain network integrity.
Think of it as an evolution of IDS technology. It incorporates detection capabilities but adds automated enforcement actions. This makes it a powerful component in a modern cybersecurity defence strategy, actively working to neutralize threats as they are identified on the network.
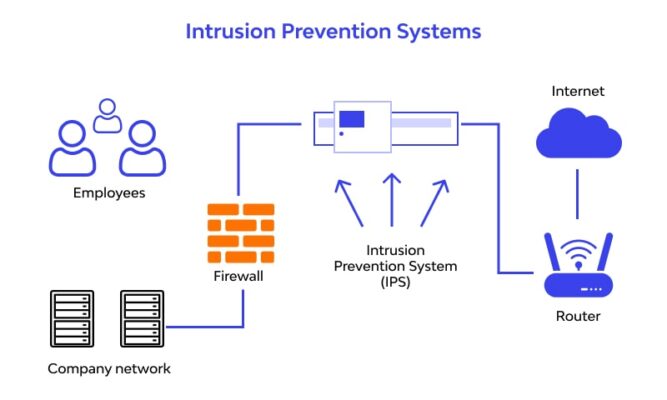
How Does an IPS Work?
Understanding how an Intrusion Prevention System operates involves looking at its deployment, inspection methods, and response capabilities. It follows a logical sequence to actively protect the network environment from incoming and sometimes outgoing threats, working continuously in the background.
Inline Deployment
A defining characteristic of an IPS is its inline deployment. This means it sits directly in the path of network communication. All network traffic destined for the protected segment must physically pass through the IPS device or software module.
Imagine it like a security checkpoint on a highway. Every vehicle (data packet) must pass through the checkpoint for inspection before proceeding. This inline placement is essential for the IPS to be able to prevent threats by blocking traffic if necessary.
Typically, an IPS is placed just behind the main network firewall. The firewall performs initial filtering based on ports and addresses. The IPS then performs deeper inspection on the traffic allowed through by the firewall, looking for more sophisticated threats hidden within legitimate-looking connections.
This strategic placement allows it to analyze communications between the internal network and the outside world (North-South traffic). It can also sometimes be placed to monitor traffic between different internal network segments (East-West traffic), depending on the security architecture and goals.
Deep Traffic Inspection
Once deployed inline, the IPS meticulously examines the data packets flowing through it. This isn’t just a surface-level check; it involves deep packet inspection (DPI). The IPS looks deep into the content and context of the data, not just the headers.
It analyzes network protocols like TCP, UDP, and application protocols such as HTTP (web traffic), SMTP (email), and DNS. The IPS checks if the protocol usage conforms to standards and looks for patterns or data known to be associated with attacks or malware.
This inspection happens in real-time as traffic passes. The system uses various detection methods, which we’ll explore next, to determine if a packet or a sequence of packets represents a threat. It’s like a security guard not just checking IDs but also inspecting baggage content.
The goal is to identify malicious payloads, exploit attempts, policy violations, or anomalous behaviour hidden within the network traffic. This requires significant processing power to avoid slowing down network communications while performing these complex analyses effectively and accurately.
Automated Response: Taking Action Instantly
The “Prevention” in IPS comes from its ability to take automated response actions when a threat is detected. Based on predefined rules and the detected threat’s severity, the IPS immediately intervenes to neutralize the danger without waiting for human intervention.
This automated response is critical for stopping fast-moving attacks before they can establish a foothold or cause damage. The specific actions an IPS can take are configurable by administrators but often include several standard responses designed to mitigate different types of threats effectively.
Common actions include blocking malicious traffic entirely by dropping the offending packets. It might also involve terminating the network connection (TCP session) between the attacker and the target, effectively cutting off the communication pathway used for the attack.
Other potential responses involve blocking all future traffic from the identified malicious IP address for a period. The IPS will also typically generate detailed security alerts for administrators and log comprehensive information about the detected event for later analysis, forensics, and reporting purposes.
How IPS Detects Threats: Key Methods Explained
Intrusion Prevention Systems employ several sophisticated techniques to identify malicious activity within the constant stream of network traffic. These methods can be used individually or, more commonly, in combination to provide broader and more accurate threat detection capabilities for organizations.

Signature-Based Detection
Signature-based detection is a foundational method used by nearly all IPS solutions. It functions by comparing patterns observed in network traffic against an extensive database of unique signatures. These signatures represent known threats like specific malware strains or exploit techniques.
Think of these signatures as digital fingerprints for malicious code or attack patterns. When data packets flow through the IPS, the system scans their content and structure, looking for matches within its signature database. It’s a pattern-matching process against documented threats.
For example, a specific sequence of commands used by a known SQL injection attack tool would have a unique signature. An IPS updated with this signature will recognize that sequence in network traffic and identify it as a SQL injection attempt, a common web application attack.
Upon matching such a signature, the IPS immediately classifies the traffic as malicious. It then triggers the pre-configured prevention action, such as blocking the malicious SQL query before it reaches the database server, thus preventing potential data theft or system compromise.
The primary strength of this method lies in its high accuracy for known threats. Well-crafted signatures generate very few false positives (incorrectly blocking legitimate traffic). This makes it reliable for stopping widespread, documented attacks efficiently and predictably for security teams.
However, its major weakness is its complete reliance on having seen the threat before. It cannot detect zero-day attacks (exploits for unknown vulnerabilities) or novel malware variants for which no signature exists yet. Protection is only as good as the latest signature update.
Therefore, maintaining an up-to-date signature database is absolutely critical. Security vendors constantly research emerging threats and distribute signature updates, often multiple times a day. Timely application of these updates is essential for the ongoing effectiveness of signature-based detection mechanisms.
Anomaly-Based Detection
Anomaly-based detection takes a different approach. Instead of looking for known bad patterns, it focuses on identifying activity that deviates significantly from normal behaviour. The IPS first establishes a baseline profile of what constitutes “normal” traffic and activity on the network.
This baseline is typically created by observing network traffic over a period and using statistical analysis or machine learning algorithms. It profiles metrics like bandwidth usage, protocols commonly used, connection durations, device communication patterns, and typical data transfer volumes between systems.
Once the baseline is established, the IPS continuously monitors network activity, comparing it against this profile of normalcy. If it detects behaviour that falls statistically outside the established baseline – for instance, a sudden surge in traffic from an unusual port – it flags it as potentially malicious.
An example could be a user account that suddenly starts accessing sensitive servers it never interacted with before, or a workstation unexpectedly initiating numerous outbound connections to unknown IP addresses late at night. These anomalies might indicate a compromised account or malware infection.
The main advantage of anomaly-based detection is its potential to detect novel or zero-day attacks that signature-based methods would miss. Since it looks for deviations rather than known patterns, it can flag previously unseen malicious behaviour or new malware variants.
However, its significant challenge lies in the potential for false positives. Legitimate but unusual network activity (like running a large backup or introducing a new application) might be incorrectly flagged as anomalous, leading the IPS to block valid traffic and disrupt operations.
Tuning anomaly-based detection requires careful configuration and ongoing learning to minimize false positives while maximizing detection rates. Defining an accurate and adaptive baseline of “normal” is complex, especially in dynamic network environments where normal behaviour frequently changes over time. Advanced systems increasingly leverage Artificial Intelligence (AI) and Machine Learning (ML).
Policy-Based Detection
Policy-based detection operates based on the security policies defined by the organization’s administrators. The IPS is configured with specific rules that dictate acceptable network behaviour and resource usage. Any traffic or activity violating these predefined policies is blocked.
For instance, a policy might state that only authorized servers can access the database containing sensitive customer information. Another policy might prohibit the use of peer-to-peer file-sharing applications or instant messaging protocols on the corporate network during business hours.
The IPS monitors network traffic to ensure compliance with these established rules. If it detects an employee’s workstation attempting to connect to the restricted database server directly, or someone trying to use a forbidden application, it identifies this as a policy violation.
Upon detecting a violation, the IPS takes action to enforce the policy. This usually involves blocking the prohibited connection or application usage. It ensures that network activity adheres strictly to the organization’s security posture and acceptable use guidelines defined by management.
This method is effective for enforcing granular control over network resources and user behaviour. It helps prevent unauthorized access, data exfiltration, and the use of potentially risky applications, aligning network activity directly with organizational security requirements and compliance mandates like HIPAA or GDPR.
The effectiveness of policy-based detection relies heavily on well-defined, comprehensive, and accurately implemented security policies. Crafting these policies requires a thorough understanding of the network environment, business needs, and potential security risks inherent in the organization’s operations. Policies must also be reviewed and updated regularly.
Stateful Protocol Analysis
Stateful protocol analysis involves the IPS having a deeper understanding of how network protocols are supposed to work. It monitors the state of network connections and analyzes the sequence of commands and data exchanges within specific protocols (like HTTP, FTP, or DNS).
The IPS compares the observed protocol activity against the expected standards and norms for that protocol. If it detects unexpected or illegitimate commands, malformed data packets, or deviations from the standard protocol handshake or transaction sequence, it flags the activity as suspicious.
For example, an attacker might try to exploit a vulnerability in a web server by sending a deliberately malformed HTTP request. An IPS using stateful protocol analysis would recognize that the request doesn’t conform to the HTTP standard and could block it, even without a specific signature.
Similarly, detecting DNS requests attempting to use unusually long domain names or specific query types might indicate a DNS tunneling attack used to exfiltrate data. The IPS understands what normal DNS traffic looks like and can flag these potentially malicious deviations based on protocol misuse.
This method can detect attacks that exploit protocol vulnerabilities or use protocols in unintended ways, which might bypass simpler detection methods. It adds a layer of context-aware security by verifying the legitimacy of protocol interactions occurring on the network traffic stream.
Like anomaly detection, stateful protocol analysis can sometimes generate false positives if legitimate applications use protocols in slightly non-standard ways. It requires the IPS vendor to have accurate and up-to-date models of various network protocols and their expected behaviours.
IPS vs. IDS: What’s the Real Difference?
One of the most common points of confusion in network security is distinguishing between an Intrusion Prevention System (IPS) and an Intrusion Detection System (IDS). While related, their functions and deployment methods differ significantly, making them distinct tools.
The core difference lies in their response to detected threats. An IDS is a passive monitoring system. It analyzes network traffic (typically a copy) and, upon detecting suspicious activity, generates alerts for security personnel. It informs you about a potential problem but doesn’t stop it directly.
In contrast, an IPS is an active system. It also analyzes traffic, but when it detects a threat, it automatically takes prevention steps, such as blocking the malicious traffic or terminating the connection. An IPS aims to stop the attack in its tracks without human intervention.
This difference in action dictates their deployment. An IDS usually sits out-of-band, monitoring a copy of the traffic (via a network tap or switch SPAN port). It doesn’t sit in the live traffic path, so it cannot block anything and doesn’t introduce latency.
An IPS, needing the ability to block, must be deployed inline, directly in the path of the network traffic. This allows it to actively filter and stop malicious packets but also means it can potentially impact network performance (latency) or block legitimate traffic if misconfigured (false positives).
Think of an IDS like a security camera system that records suspicious activity and alerts guards. An IPS is like an active security turnstile or gate that physically prevents unauthorized individuals (malicious packets) from entering the premises based on real-time checks.
Often, organizations use both IDS and IPS technologies together. An IDS might provide broader visibility and detailed logging for analysis, while the IPS handles the immediate blocking of critical, high-confidence threats, offering a layered approach combining detection depth with active prevention.
IPS vs. Firewall
Another common question is how an Intrusion Prevention System differs from a Firewall. While both are critical network security components controlling traffic flow, they operate at different levels and look for different things. They serve distinct, complementary roles in protecting a network.
A traditional Firewall primarily acts as a filter based on network and transport layer information. It makes decisions based on predefined rules involving source/destination IP addresses, port numbers, and protocols (like TCP, UDP, ICMP). It’s like a basic traffic cop directing cars based on license plates and destinations.
Firewalls are excellent at enforcing network segmentation and blocking access to or from specific known addresses or services. However, they generally don’t inspect the content of the allowed traffic. Malicious code hidden within seemingly legitimate web traffic on port 80 might pass straight through a basic firewall.
An IPS operates at a deeper level. It performs deep packet inspection (DPI), analyzing the actual data payload and application behaviour within the traffic allowed by the firewall. It looks for exploit code, malware signatures, protocol anomalies, or policy violations inside the communication stream.
Think of the firewall as controlling which doors are open, while the IPS inspects who and what is trying to come through those open doors. An IPS can detect and block attacks like SQL injection, cross-site scripting (XSS), or malware downloads that a traditional firewall would likely miss.
Therefore, an IPS does not replace a firewall; it complements it. The standard architectural practice is to place the IPS behind the firewall. The firewall provides the first line of defence, filtering out unwanted traffic based on coarser rules, reducing the load on the IPS.
The IPS then scrutinizes the remaining traffic, providing a more sophisticated layer of threat prevention against advanced attacks. Modern Next-Generation Firewalls (NGFW) and Unified Threat Management (UTM) appliances often integrate both firewall and IPS capabilities (along with other security functions) into a single device.
Types of Intrusion Prevention Systems
Intrusion Prevention Systems are not one-size-fits-all. They come in different forms, categorized primarily by where they are deployed and what part of the IT infrastructure they are designed to protect. Understanding these types helps organizations choose the most appropriate solutions.
Network-Based IPS (NIPS)
A Network-based Intrusion Prevention System (NIPS) is typically a dedicated hardware appliance deployed at strategic points within the network infrastructure. Its purpose is to monitor and control traffic flowing across network segments, often protecting the entire network perimeter or critical internal zones.
NIPS devices analyze traffic passing between networks, such as between the internet and the internal corporate network, or between different internal departments or data center segments. They inspect all packets flowing through them for signs of malicious activity or policy violations.
By sitting at key network junctions, a NIPS provides broad protection against threats attempting to enter or move laterally within the network. Examples include detecting and blocking incoming malware, external scanning attempts, or worms trying to propagate across internal subnets.
They are essential for protecting servers, applications, and multiple users simultaneously by scrutinizing aggregate network traffic. However, they generally lack visibility into encrypted traffic streams (unless SSL/TLS decryption is configured) and activities occurring solely within an individual host computer. Scalability and throughput capacity are key considerations.
Host-Based IPS (HIPS)
A Host-based Intrusion Prevention System (HIPS) is a software application installed directly on an individual endpoint device, such as a server, workstation, or laptop. Unlike NIPS which monitors network traffic, HIPS focuses on the activities occurring on the specific host it protects.
HIPS monitors system calls, application behaviour, file system modifications, registry changes (on Windows), and local network traffic entering and leaving the host. It looks for suspicious actions that might indicate malware infection, unauthorized access attempts, or policy violations originating from or targeting that specific device.
For example, HIPS could detect and block malware attempting to modify critical system files, prevent an unauthorized application from accessing sensitive data, or stop suspicious outbound connections initiated by spyware installed on the host. It provides granular protection at the endpoint level.
HIPS offers deep visibility into host-specific activities and can stop threats that might bypass network-level defenses (NIPS), especially encrypted threats. It is a critical component of endpoint security strategies but requires deployment and management across numerous individual devices, which can be resource-intensive.
Wireless IPS (WIPS)
A Wireless Intrusion Prevention System (WIPS) is specifically designed to monitor and protect an organization’s wireless networks (Wi-Fi). It scans the radio frequency spectrum used by Wi-Fi devices to detect and mitigate wireless-specific threats and enforce wireless security policies.
WIPS looks for threats such as rogue access points (unauthorized APs connected to the corporate network), evil twin attacks (APs impersonating legitimate ones to steal credentials), ad-hoc networks, denial-of-service attacks against the wireless infrastructure, or improperly configured legitimate access points.
Upon detecting a wireless threat, a WIPS can take actions like locating the rogue device, disconnecting unauthorized clients, preventing connections to malicious APs, or sending alerts to administrators. It acts as the dedicated security guard for the Wi-Fi environment.
WIPS is essential for organizations that rely heavily on wireless connectivity, ensuring that the convenience of Wi-Fi doesn’t create significant security vulnerabilities. It protects against unauthorized access and attacks targeting the unique characteristics of wireless communication protocols and deployments.
Other Types
Beyond the main categories, other related technologies exist. Cloud IPS refers to IPS capabilities delivered as a cloud service, often integrated into cloud provider offerings (like AWS GuardDuty or Azure Firewall Premium) or provided by third-party Security-as-a-Service vendors to protect cloud workloads and infrastructure.
Network Behavior Analysis (NBA) systems focus heavily on detecting threats by monitoring broad network traffic patterns and flows for anomalies. While often overlapping with anomaly-based NIPS, NBA solutions typically emphasize network-wide behavioral shifts, sometimes using NetFlow or other flow data rather than full packet inspection.
Why Use an IPS? Key Benefits for Your Security
Implementing an Intrusion Prevention System offers significant advantages for an organization’s overall cybersecurity posture. These benefits stem from its ability to actively and automatically stop threats, enforce policies, and provide deeper visibility into network activities compared to passive defenses alone.
- Proactive Threat Prevention: The primary benefit is stopping attacks before they succeed. By blocking malicious traffic in real-time, IPS significantly reduces the likelihood of data breaches, malware infections, system downtime, and associated recovery costs.
- Automated Response: Automation is key. IPS reacts instantly to detected threats without needing human intervention, which is crucial for combating fast-moving automated attacks that can cause damage in seconds or minutes. This frees up security teams for more strategic tasks.
- Reduced Security Team Workload: By handling the immediate blocking of many common threats automatically, an IPS reduces the number of alerts security analysts need to investigate manually, allowing them to focus on more complex incidents and proactive threat hunting.
- Security Policy Enforcement: IPS helps consistently enforce organizational security policies across the network, blocking unauthorized applications, access attempts, or data movements that violate predefined rules, thereby reducing insider threats and accidental risks.
- Compliance Assistance: Many industry regulations and standards (like PCI-DSS for payment cards, HIPAA for healthcare) mandate intrusion detection and prevention capabilities. Implementing an IPS helps organizations meet these compliance requirements and avoid potential penalties.
- Protection Against Diverse Threats: Modern IPS solutions, using multiple detection methods, can protect against a wide range of attacks, including known malware, network exploits, vulnerability scanning, denial-of-service attempts, and potentially some zero-day threats (via anomaly detection).
- Increased Network Visibility: The analysis performed by an IPS provides valuable insights into the types of threats targeting the network, traffic patterns, and application usage, aiding in security posture assessment and future planning.
Are There Downsides? Understanding IPS Limitations
While highly beneficial, Intrusion Prevention Systems are not a silver bullet and come with their own set of limitations and challenges. Understanding these potential drawbacks is essential for effective implementation and managing expectations regarding their capabilities within a security framework.
- False Positives: Perhaps the most significant challenge. If not properly tuned, an IPS (especially using anomaly-based detection) can misidentify legitimate traffic as malicious and block it. This can disrupt critical business operations and frustrate users, requiring careful configuration and monitoring.
- False Negatives: No security system is perfect. Sophisticated, novel, or heavily obfuscated attacks might evade detection, leading to a false negative – the IPS fails to stop a real threat. Over-reliance on IPS without other security layers is risky.
- Performance Impact: Because IPS devices sit inline and perform deep inspection, they require substantial processing power. An under-provisioned IPS can become a network bottleneck, introducing latency and reducing network throughput, potentially impacting application performance.
- Encrypted Traffic Blindness: Standard IPS cannot inspect the contents of encrypted traffic streams (like HTTPS/SSL/TLS). Attackers increasingly use encryption to hide malicious payloads. Inspecting encrypted traffic requires the IPS to perform decryption/re-encryption, adding significant complexity, cost, and potential privacy concerns.
- Complexity in Configuration & Tuning: Setting up and maintaining an IPS effectively requires expertise. Defining appropriate policies, tuning detection engines to minimize false positives without increasing false negatives, and managing signature updates demands skilled security personnel.
- Signature Dependency: Signature-based detection, while reliable for known threats, is inherently reactive. It offers no protection against zero-day exploits until a signature is developed and deployed, leaving a window of vulnerability for organizations.
Where Does IPS Fit in Your Security Strategy?
An Intrusion Prevention System is a vital component, but only one piece of a comprehensive cybersecurity strategy. It operates most effectively as part of a layered security approach, often referred to as defense-in-depth. No single tool can protect against all threats.
IPS works in conjunction with other security controls. It complements the Firewall, which provides essential perimeter control and traffic filtering based on ports and protocols. The IPS adds a layer of deeper inspection for threats the firewall might miss within allowed traffic streams.
It can also work alongside an Intrusion Detection System (IDS). While seeming redundant, an IDS might be tuned for broader detection with higher tolerance for false positives (since it only alerts), providing visibility that a tightly tuned IPS (focused on accurate blocking) might miss.
Furthermore, IPS protection should be integrated with endpoint security (like HIPS, antivirus, EDR – Endpoint Detection and Response), email security gateways, web application firewalls (WAFs), and Security Information and Event Management (SIEM) systems for centralized logging, correlation, and incident response coordination.
The placement and configuration of an IPS within the network security architecture depends on the organization’s specific risks, assets, and topology. It might protect the main internet gateway, internal data center segments, specific critical servers, or even cloud environments, often integrated within NGFW or UTM platforms.
Ultimately, an IPS strengthens the overall security posture by providing active, automated prevention against a significant portion of network-based threats. It’s a crucial element for reducing risk but must be supported by other security technologies, processes, and skilled personnel to be truly effective.
In today’s complex threat landscape, simply detecting intrusions is often not enough. An Intrusion Prevention System (IPS) serves as an essential active defender, moving beyond passive monitoring to automatically block and neutralize threats in real-time before they compromise valuable systems and data.
