This article serves as your friendly guide to understanding firewalls. We’ll break down exactly what they are, explore how they function behind the scenes, and explain why they are absolutely essential for your online safety. We aim to make this complex topic simple and clear.
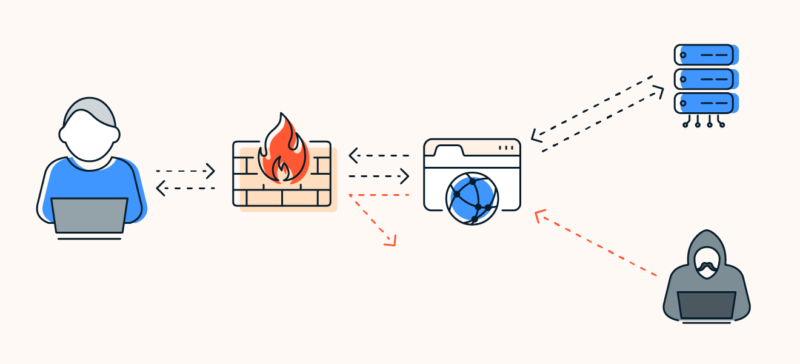
So, what is a firewall? A firewall is a security system that monitors network traffic, deciding whether to allow or block specific data based on a set of security rules. It acts as a crucial barrier between your trusted internal network and the untrusted outside world.
What is a Firewall?
A firewall is a network security system designed to monitor and control incoming and outgoing network traffic based on security rules. Its primary goal is to create a barrier between trusted internal networks and untrusted external networks. Firewalls are often the first line of defense against unauthorized access, attacks, and cyber threats that could compromise your system. They can be hardware or software-based and are used in both personal and corporate environments.

How does a firewall work?
At a high level, firewalls work by establishing security rules and then filtering traffic based on these rules. The firewall inspects data packets as they try to pass through it. Here’s a simple breakdown of how it works:
- Traffic Inspection: Every packet that enters or exits the network is checked by the firewall.
- Rule Evaluation: The firewall compares each packet to a set of defined rules. These rules determine whether the packet should be allowed or blocked based on its source, destination, and other characteristics.
- Decision Making: If the packet matches a rule that allows it through, it’s accepted. Otherwise, the packet is blocked.
- Logging and Reporting: Many firewalls log these interactions, so administrators can analyze network activity and respond to potential threats.
This process is continuous and happens in real-time, ensuring that any unauthorized data or harmful malware is quickly blocked.
Why Are Firewalls So Important? Key Benefits
Understanding what a firewall is leads to the next crucial question: why do you need one? Firewalls are fundamentally important because they serve as the primary defense mechanism against a vast array of online threats, safeguarding your devices, data, and privacy in multiple critical ways.
Your First Line of Defense Against Hackers
One of the most vital roles of a firewall is preventing unauthorized users, including hackers and malicious bots, from gaining access to your computer or network. Automated tools constantly scan the internet for vulnerable devices, probing for open doors (ports) to exploit.
A firewall effectively makes your devices invisible or inaccessible to many of these scans. It blocks unsolicited incoming connection requests, significantly reducing the chances of a remote attacker finding a way in. This protection is active 24/7, constantly shielding your digital perimeter from intrusion attempts.
Stopping Malicious Software in its Tracks
Firewalls also play a role in preventing certain types of malicious software (malware) from infecting your system or spreading. They can block access to websites known to host malware or block communication attempts from malware already on a network trying to “phone home” to a command-and-control server.
However, it’s crucial to understand this: a firewall is not a substitute for dedicated antivirus or anti-malware software. While it blocks certain network pathways malware might use, it doesn’t typically scan files or detect viruses already present. Think of them as complementary tools working together for robust protection.
Controlling What Comes In and Goes Out
Firewalls provide essential control over the types of data communication allowed to and from your network. This is based on the security policy, which dictates which applications, services, or protocols are permitted. This control helps ensure network resources are used appropriately and securely.
For example, a business might configure its firewall to allow employees access to work-related websites and email but block access to streaming services or online games during work hours. This enforces company policy and can also preserve network bandwidth for essential tasks.
Creating Safer Zones Online
By preventing unauthorized intrusions and controlling traffic, firewalls contribute significantly to protecting your sensitive personal and financial data. They help prevent attackers from accessing stored information or intercepting data as it travels across less secure parts of the network. This contributes greatly to your overall online privacy.
Furthermore, within larger organizations or even sophisticated home networks, firewalls can be used internally. They segment the network into different security zones. For example, a guest Wi-Fi network can be firewalled off from the main network containing sensitive files, limiting potential damage if a guest device is compromised.
Types of Firewalls
There are several types of firewalls, each with different features and levels of protection. Understanding the different types can help you decide which is best for your needs.
1. Packet-Filtering Firewalls
Packet-filtering firewalls are one of the oldest and simplest types of firewalls. They work by examining packets of data that are transmitted across the network. Each packet is checked against a set of predefined rules based on attributes like IP addresses, ports, and protocols. If the packet matches the allowed criteria, it is permitted; if not, it is blocked. While packet-filtering firewalls are effective in blocking unauthorized access, they do not inspect the content of the traffic, which can make them less secure.
2. Stateful Inspection Firewalls
Stateful inspection firewalls are more advanced than packet-filtering firewalls. Instead of only looking at individual packets, they keep track of the state of network connections. This means that they can determine whether a packet is part of an ongoing, legitimate connection or if it’s coming from an unauthorized source. This makes stateful inspection firewalls better at identifying and blocking malicious attacks while allowing legitimate communication to pass through.
3. Proxy Firewalls
Proxy firewalls, also known as application-layer firewalls, work differently from traditional firewalls. Instead of simply filtering packets, they act as intermediaries between the internal network and the outside world. When an internal device sends a request to the internet, the proxy firewall intercepts the request and sends it on behalf of the device. This adds a layer of anonymity and helps protect internal systems from direct exposure to external threats.
4. Next-Generation Firewalls (NGFW)
Next-generation firewalls (NGFW) combine the features of traditional firewalls with additional security functions. NGFWs integrate features like deep packet inspection (DPI), intrusion prevention systems (IPS), application awareness, and cloud-delivered threat intelligence. These features make NGFWs highly effective at detecting and blocking sophisticated attacks. NGFWs are suitable for enterprises and businesses that require advanced security measures for complex networks.
Firewall Features and Functions
Firewalls are equipped with several important features that enhance network security. Here are some key functions:
Traffic Monitoring and Filtering
Firewalls monitor network traffic, checking for suspicious activities. This includes watching for any unusual spikes in data transmission or unauthorized access attempts. By filtering this traffic, firewalls can prevent harmful data from entering the network.
Access Control Policies
Firewalls allow administrators to set up specific access rules. For example, you might allow traffic from trusted sources (like a corporate VPN) but block everything else. These rules are essential for controlling who can access the network and under what conditions.
VPN Support
Many modern firewalls support Virtual Private Networks (VPNs), which create a secure, encrypted tunnel for remote users to access a network. This is particularly useful for businesses with remote workers or for securely connecting different network locations.
Logging and Reporting
An often-overlooked feature, logging and reporting help administrators track network activity and investigate any incidents. With detailed logs, you can trace what happened during a potential attack or unauthorized access attempt, aiding in swift response.
Firewall vs. Other Security Tools: What’s the Difference?
It’s easy to get confused by the various security tools available. It’s important to understand that firewalls are just one piece, albeit a crucial one, of a larger security puzzle. They work best as part of a team, complementing other tools with different functions.
Firewall vs. Antivirus
This is a common point of confusion. A firewall controls network traffic flow (like a bouncer), while antivirus software detects and removes malicious files and code already on your device (like a doctor). They address different types of threats.
A firewall might block access to a website known to distribute malware, preventing the download in the first place. But if malware arrives via another method (like a USB drive or a permitted email attachment), the firewall likely won’t catch it. That’s where antivirus software steps in to scan files and neutralize the threat. You need both.
Firewall vs. VPN
Firewalls and VPNs (Virtual Private Networks) also serve distinct primary purposes. A firewall filters traffic based on rules, whereas a VPN creates a secure, encrypted connection (a tunnel) between your device and a remote server, often used for privacy or accessing resources remotely.
A VPN encrypts your traffic, making it unreadable to eavesdroppers on public Wi-Fi, and can mask your real IP address. A firewall doesn’t inherently encrypt general traffic but controls which traffic is allowed. They can be used together; for instance, you might connect to your work network via a VPN, and the work network’s firewall still controls what you can access.
Firewall FAQs
What is the difference between a stateful and stateless firewall?
A stateful firewall tracks the state of active connections, allowing it to make more intelligent decisions about whether to allow or block traffic. A stateless firewall, however, treats each packet in isolation, without context, making it less effective against sophisticated attacks.
How do firewalls protect against malware?
Firewalls help prevent malware from entering the network by blocking suspicious or unauthorized traffic. They can also scan for malware signatures in incoming data and prevent harmful software from being executed.
Can a firewall prevent all cyber-attacks?
While firewalls are essential for protecting networks, they cannot prevent all types of cyberattacks. For example, firewalls cannot stop phishing attacks or malware that enters through authorized users. Additional security measures are needed.
Firewalls are an indispensable tool in modern network security. They act as a gatekeeper, protecting against unauthorized access, malware, and other cyber threats. Understanding how firewalls work, the different types available, and how they integrate into a larger security strategy is essential for maintaining a secure digital environment.
Whether you’re a home user, a small business owner, or an IT professional, implementing the right firewall solution is crucial for safeguarding your network. With proper configuration and regular monitoring, firewalls can provide robust protection against the ever-evolving landscape of cyber threats.
