DDoS attacks disrupt online services by flooding them with malicious traffic. This guide explains what DDoS attacks are, how they work, and how to identify them. We’ll explore common attack types like volumetric, protocol, and application layer attacks. Crucially, we’ll cover the mitigation process, from proactive defense strategies to reactive measures and post-attack analysis, equipping you to protect your online assets effectively.
What is DDoS Attack?
A DDoS attack, or Distributed Denial of Service attack, is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming it with a flood of internet traffic from multiple sources. Think of it like a digital traffic jam, where a massive number of cars suddenly flood a small street, making it impossible for anyone to pass. This disruption aims to make online services unavailable to legitimate users.
Unlike a simple Denial of Service (DoS) attack, which originates from a single source, a DDoS attack harnesses the power of a botnet. Imagine a swarm of remotely controlled computers, all working together to flood the target with requests. These compromised machines, often infected with malware, are the “soldiers” in this digital assault, creating a massive wave of traffic that the target server simply can’t handle. This network of infected devices is what makes a DDoS so powerful and difficult to defend against.
The core principle behind a DDoS is overwhelming the target’s resources. Whether it’s a website, an online game server, or a critical network infrastructure, the goal is the same: to make it inaccessible. This is achieved by flooding the target with a massive volume of traffic, consuming its bandwidth and processing power. The result is a system that slows down, crashes, or becomes completely unavailable to legitimate users.
For instance, consider a popular e-commerce website during a peak shopping season. If attackers launch a DDoS attack, they can flood the website’s servers with so many requests that it becomes unresponsive. Customers trying to browse or make purchases are met with slow loading times or error messages, leading to lost sales and potential damage to the company’s reputation. This is why DDoS attacks are a serious threat for businesses that rely on online presence.
Essentially, a DDoS attack is a coordinated effort to disrupt online services by flooding them with excessive traffic. This flood of data, originating from numerous compromised devices, overwhelms the target’s resources, causing it to become unavailable to legitimate users. Understanding this fundamental definition is the first step in comprehending the severity and impact of these cyberattacks.
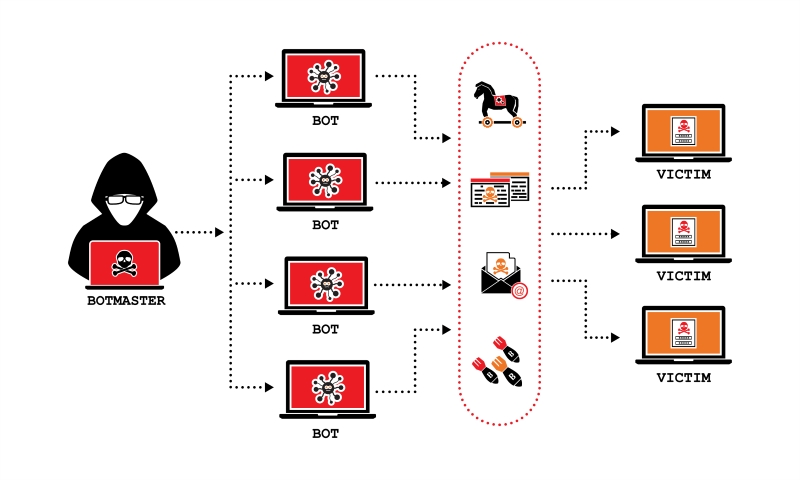
How Does a DDoS Attack Work?
A DDoS attack works by overwhelming a target server or network with a flood of traffic from multiple compromised computer systems, known as a botnet. Think of it as a digital mob, where numerous devices, unknowingly controlled by an attacker, simultaneously bombard the target. This coordinated assault aims to exhaust the target’s resources, rendering it unavailable to legitimate users. The process involves several key stages, each contributing to the overall disruption.
The attack typically begins with the creation of a botnet. This network of compromised devices, often personal computers, IoT devices, or even servers, is infected with malware that allows the attacker to control them remotely. These infected devices, or “bots,” are spread through various methods, including phishing emails, malicious downloads, and exploiting software vulnerabilities. Once a sufficient number of devices are compromised, the attacker can orchestrate a coordinated attack.
When the attacker initiates the DDoS attack, they send commands to the botnet, instructing the compromised devices to send a flood of traffic to the target’s IP address. This traffic can take various forms, depending on the type of attack. For example, in a UDP flood, the bots send a massive number of UDP packets to the target, overwhelming its network bandwidth. In an HTTP flood, the bots send a barrage of HTTP requests, exhausting the server’s processing power.
The target server, faced with this overwhelming influx of traffic, struggles to process legitimate requests. As its resources become saturated, the server slows down, crashes, or becomes completely unresponsive. Legitimate users attempting to access the service are met with slow loading times, error messages, or complete unavailability. The attack effectively disrupts normal operations, causing downtime and potential financial losses for the target.
To illustrate, imagine a popular online gaming server. During a DDoS attack, the server is flooded with fake player connections, consuming its bandwidth and processing power. Legitimate players experience severe lag, disconnections, and an inability to join the game. This disruption not only ruins the gaming experience but also damages the game’s reputation and potentially drives players away. This example highlights the disruptive nature of DDoS attacks and their impact on online services.
How to Identify a DDoS Attack
Identifying a DDoS attack involves recognizing unusual patterns in network traffic and server performance that indicate an overwhelming influx of malicious requests. Detecting these attacks early is crucial for implementing mitigation strategies and minimizing downtime. It’s like diagnosing a sudden illness in your online infrastructure; you need to spot the symptoms quickly.
1. Sudden and Unexplained Slowdowns
One of the most common signs of a DDoS attack is a sudden and significant slowdown in website or service performance. Users may experience unusually long loading times, frequent timeouts, or complete unavailability. This is often the first indicator that something is amiss. For example, a website that normally loads in seconds suddenly takes minutes to respond, or fails to respond at all. This abrupt change in performance is a red flag.
2. Unusual Traffic Spikes
Monitoring network traffic is essential for identifying DDoS attacks. A sudden and dramatic increase in traffic, especially from multiple IP addresses, can signal an attack. This spike is often far beyond the normal traffic patterns of the targeted service. Analyzing traffic logs and using network monitoring tools can help detect these anomalies. Imagine a normally steady flow of traffic on a website suddenly surging to ten or a hundred times its normal volume.
3. Server Resource Exhaustion
DDoS attacks aim to overwhelm server resources, leading to high CPU usage, memory consumption, and bandwidth utilization. If server performance metrics show unusually high resource usage without a corresponding increase in legitimate user activity, it could be a sign of an attack. This is because the sheer volume of malicious requests consumes system resources, leaving little for legitimate users. For instance, a server that normally operates at 20% CPU usage suddenly spikes to 100%.
4. Multiple Requests from the Same IP
While not always indicative of a DDoS attack, a sudden influx of requests from a large number of unique IP addresses can be a warning sign. Attackers often use botnets, which consist of numerous compromised devices, to generate traffic. Observing a large number of requests from diverse locations within a short time frame can point towards an attack. However, this must be taken in context, as some services can experience sudden normal traffic increases.
5. Specific Error Messages
Some DDoS attacks can trigger specific error messages on the target server, such as “service unavailable” or “connection timed out.” These errors can provide clues about the nature of the attack and the type of traffic being used. If these errors occur during periods of unusual traffic, a DDoS attack should be considered. Furthermore, some attacks will overwhelm specific services, resulting in errors only for those services.
6. Increased Logins and Failed Logins
A sudden surge in login attempts, particularly failed login attempts, can indicate a brute-force attack, which is sometimes used in conjunction with DDoS attacks. This activity can overwhelm authentication servers and disrupt legitimate user access. Monitoring login activity and implementing rate limiting can help mitigate this risk. Large numbers of failed logins could indicate a botnet trying various credentials.
What are some common types of DDoS attacks?
DDoS attacks vary in their methods, each targeting different aspects of a server or network. Understanding these types is crucial for effective mitigation. Generally, they fall into three main categories: volumetric attacks, protocol attacks, and application layer attacks. Each type exploits different vulnerabilities and requires specific defense strategies.
1. Volumetric Attacks
Volumetric attacks aim to overwhelm the target’s network bandwidth with a massive flood of traffic. These attacks are like trying to push a river through a garden hose; the sheer volume of data clogs the network, making it impossible for legitimate traffic to pass. This type of attack focuses on saturating the network’s capacity, leading to service disruption.
One common example is the UDP flood. User Datagram Protocol (UDP) is a connectionless protocol, meaning it doesn’t require a handshake before sending data. In a UDP flood, attackers send a massive number of UDP packets to random ports on the target server. The server tries to process these packets and respond, quickly exhausting its resources. Imagine thousands of small, unsolicited packages arriving at a post office, overwhelming the staff.
Another prevalent volumetric attack is the ICMP flood. Internet Control Message Protocol (ICMP) is used for network diagnostics and error reporting. In an ICMP flood, attackers send a barrage of ICMP echo requests (pings) to the target server. The server responds to each request, consuming bandwidth and processing power. This is similar to someone constantly calling a business and immediately hanging up, tying up the phone lines.
DNS amplification attacks also fall under the volumetric category. Attackers exploit vulnerabilities in Domain Name System (DNS) servers to amplify the volume of traffic. They send small DNS queries to open DNS resolvers, but spoof the source IP address to be the target’s IP. The DNS resolvers respond with much larger responses, sending them to the target. This amplification effect can generate a massive amount of traffic, overwhelming the target’s network. This is like a tiny whisper being amplified into a deafening roar.
These volumetric attacks are often measured in bits per second (bps) and are designed to consume the network’s bandwidth, making it unavailable to legitimate users. Mitigation involves using techniques like traffic scrubbing, which filters out malicious traffic, and content delivery networks (CDNs), which distribute traffic across multiple servers. Properly configured firewalls and intrusion prevention systems are also critical defenses.
2. Protocol Attacks
Protocol attacks exploit vulnerabilities in network protocols to consume server resources. Instead of flooding the network with sheer volume, these attacks target specific protocols, such as TCP and SYN, to exhaust the server’s connection state tables. This type of attack aims to disrupt the server’s ability to maintain connections, leading to service unavailability.
A classic example is the SYN flood. Transmission Control Protocol (TCP) requires a three-way handshake to establish a connection: SYN, SYN-ACK, and ACK. In a SYN flood, attackers send a large number of SYN requests to the target server but never complete the handshake. The server allocates resources for each incomplete connection, eventually running out of resources. This is similar to someone calling a restaurant and reserving every table but never showing up.
Another protocol attack is the Ping of Death. Attackers send oversized ICMP packets to the target server, exceeding the maximum allowed size. The server struggles to process these fragmented packets, leading to crashes or system instability. This attack exploits a vulnerability in how servers handle fragmented packets. This is like sending a package that is too large for the postal service to handle, causing a system wide failure.
Protocol attacks are often measured in packets per second (pps) and focus on exhausting the server’s connection state tables. Mitigation involves using techniques like SYN cookies, which prevent the server from allocating resources for incomplete connections, and rate limiting, which restricts the number of connections from a single IP address. Firewalls and intrusion detection systems can also help identify and block malicious traffic.
3. Application Layer Attacks
Application layer attacks target specific application services to exhaust server resources. These attacks focus on disrupting the application layer (Layer 7) of the OSI model, targeting specific web applications or services. They are often more sophisticated and harder to detect than volumetric or protocol attacks, as they mimic legitimate traffic.
HTTP floods are a common example. Attackers send a massive number of HTTP requests to the target web server, overwhelming its processing power. These requests can be GET or POST requests, designed to consume server resources. This is like a crowd of people repeatedly asking a store clerk for help, overwhelming their ability to assist customers.
Another application layer attack is the Slowloris attack. Attackers send partial HTTP requests to the target server, keeping the connections open for extended periods. The server allocates resources for each open connection, eventually running out of resources. This is like someone calling a business and holding the line indefinitely, preventing others from calling.
These attacks are often measured in requests per second (rps) and focus on exhausting the server’s application resources. Mitigation involves using techniques like web application firewalls (WAFs), which can filter out malicious HTTP requests, and load balancing, which distributes traffic across multiple servers. Intrusion detection systems and rate limiting are also crucial defenses.
What is the process for mitigating a DDoS attack?
The process for mitigating a DDoS attack involves a combination of proactive measures to prevent attacks and reactive steps to minimize their impact when they occur. It’s about building a strong defense and having a clear plan of action. Effective mitigation requires a multi-layered approach, addressing different aspects of the attack.
1. Proactive Measures: Building a Strong Defense
Proactive measures focus on preventing DDoS attacks before they happen. This involves implementing security best practices and infrastructure improvements. Strong network architecture is crucial. Utilizing load balancing to distribute traffic across multiple servers helps absorb attack volume. Properly configured firewalls and intrusion prevention systems (IPS) can block known attack patterns.
Rate limiting is another essential proactive step. By restricting the number of requests from a single IP address, you can prevent attackers from overwhelming your servers. This also helps mitigate brute-force attacks. Implementing connection limits further prevents resource exhaustion. Web application firewalls (WAFs) are vital for protecting web applications from application-layer attacks. They filter out malicious HTTP requests and block known attack patterns.
Content delivery networks (CDNs) enhance security and performance. Distributing traffic across multiple servers and caching static content reduces server load. DNS security, including DNSSEC, prevents DNS spoofing and amplification attacks. Regular security audits are vital. Conducting assessments and patching systems prevents exploits. Finally, having an incident response plan ensures a coordinated response during an attack.
For example, imagine a company that implements a CDN. The CDN distributes website traffic across a network of servers. If a DDoS attack occurs, the CDN absorbs much of the attack traffic, preventing the origin server from being overwhelmed. This significantly reduces the impact of the attack. Furthermore, a company that utilizes a WAF can block specific types of HTTP flood attacks, preventing the application layer from being compromised.
2. Reactive Measures: Responding to an Attack
When a DDoS attack occurs, reactive measures are crucial for minimizing its impact. Traffic monitoring and analysis are essential for detecting anomalies. Network monitoring tools and security information and event management (SIEM) systems provide real-time insights into network traffic. Traffic scrubbing filters malicious traffic through specialized services. Diverting traffic to scrubbing centers allows for analysis and filtering.
Cloud-based DDoS protection offers scalable mitigation. Cloud providers offer infrastructure and expertise to handle large-scale attacks. Collaboration with ISPs and law enforcement is vital. ISPs can help mitigate attacks, and law enforcement can investigate perpetrators. Communication is crucial. Maintaining open communication with users and stakeholders manages expectations.
For instance, consider a company that utilizes cloud-based DDoS protection. When an attack occurs, the cloud provider’s infrastructure absorbs the malicious traffic, preventing the company’s servers from being overwhelmed. The cloud provider’s expertise allows for rapid mitigation and minimizes downtime. Additionally, a company that has established communication channels with their ISP can work together to block malicious traffic sources.
3. Post-Attack Analysis: Learning and Improving
After a DDoS attack, a thorough post-attack analysis is essential. Identifying the root cause helps prevent future attacks. Documenting lessons learned improves mitigation strategies. Implementing necessary security improvements strengthens defenses. This continuous improvement cycle is critical for maintaining resilience against evolving threats.
For example, a company that experiences a DDoS attack analyzes the attack logs to identify the attack vectors and sources. They then update their WAF rules to block similar attacks in the future. They also conduct a security audit to identify and patch any vulnerabilities that were exploited. This process helps them build a stronger defense against future attacks.
